Security News

Partner Content There are plenty of technology acronyms in the alphabet soup of the cybersecurity industry, but DSPM is the latest one leading the charge; its recent buzz has brought scrutiny to various security concepts that have cluttered the meaning behind data security posture management. DSPM provides visibility into where sensitive data is located, who has access to it, how it's being used, and how the security controls and permissions are configured on the data stores or applications hosting the data.

Microsoft Copilot has been called one of the most powerful productivity tools on the planet. Copilot is an AI assistant that lives inside each of your Microsoft 365 apps — Word, Excel, PowerPoint,...

Automated API security testing predominantly uses tools from two application security methodologies: static application security testing and dynamic application security testing. API security testing is increasingly being integrated into the API security offering, translating into much more efficient processes, such as automatically associating appropriate APIs with suitable test cases.

2024 will be a revolutionary year for the data security landscape as Data Security Posture Management technology rapidly evolves to keep pace with the colossal amount of data being created, stored and shared within organizations and across business sectors, according to Metomic. By implementing security solutions that enable security professionals to see exactly where data is stored and shared, as well as who has access to it, organizations will be better equipped to detect, connect, and protect sensitive data across their entire cloud estate, from one unified platform.

WordPress administrators are being emailed fake WordPress security advisories for a fictitious vulnerability tracked as CVE-2023-45124 to infect sites with a malicious plugin. The emails pretend to be from WordPress, warning that a new critical remote code execution flaw in the platform was detected on the admin's site, urging them to download and install a plugin that allegedly addresses the security issue.

In July 2023, the Association of Southeast Asian Nations officially opened a joint cyber security information sharing and research centre, or Cybersecurity and Information Centre of Excellence, in a bid to increase the region's shared cyber threat defences. At the opening of the ACICE, Singapore's Ministry of Defence said Singapore alone experienced a 174% increase in phishing attempts between 2021 and 2022, while Southeast Asia cyber crime had increased 82%. Recorded Future Chief Information Security Officer Jason Steer told TechRepublic some customers in the region felt digitisation was turning data from gold into uranium due to cyber risk.

Infosec in brief The European Union's Parliament and Council have reached an agreement on the Cyber Resilience Act, setting the long-awaited security regulation on a path to final approval and adoption, along with new rules exempting open source software. The CRA was proposed by the European Commission in September 2022 and imposes mandatory cyber security requirements for all hardware and software products - from baby monitors to routers, as the EU Commission put it.

"The security technology market is in a state of general overload with pressure on budgets, staff hiring/retention, and having too many point solutions are pervasive issues for organizations today." Security and risk management leaders should evaluate how security orchestration, automation and response can support and optimize their broader security operations by automating repetitive tasks; triaging security incidents faster with automated investigation and response; increasing productivity, efficiency and accuracy; and strengthening defenses by connecting and coordinating complex workflows across their team and tools.

Apple recommends users update to iOS 17.1.2, iPadOS 17.1.2 and macOS 14.1.2. Apple has patched two zero-day vulnerabilities affecting iOS, iPadOS and macOS; users are advised to update to iOS 17.1.2, iPadOS 17.1.2 and macOS 14.1.2.
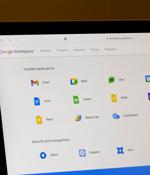
Cybersecurity researchers from the firm Hunters discovered a vulnerability in Google Workspace that could allow unwanted access to Workspace APIs.According to the Hunters team, the vulnerability is based on Google Workspace's role in managing user identities across Google Cloud services.