Security News

Trojan titan TrickBot has added a striking anti-debugging feature that detects security analysis and crashes researcher browsers before its malicious code can be analyzed. The new anti-debugging feature was discovered by Security Intelligence analysts with IBM, who reported the emergence of a variety of TrickBot tactics aimed at making the job of security researcher more difficult, including server-side injection delivery and secure communications with the command-and-control server to keep code protected.

The notorious TrickBot malware has received new features that make it more challenging to research, analyze, and detect in the latest variants, including crashing browser tabs when it detects beautified scripts. TrickBot has dominated the malware threat landscape since 2016, constantly adding optimizations and improvements while facilitating the deployment of damaging malware and ransomware strains.

Cybersecurity researchers have disclosed details of a now-patched bug in Box's multi-factor authentication mechanism that could be abused to completely sidestep SMS-based login verification. "Using this technique, an attacker could use stolen credentials to compromise an organization's Box account and exfiltrate sensitive data without access to the victim's phone," Varonis researchers said in a report shared with The Hacker News.

A team of researchers at the Universities of Arizona, Georgia, and South Florida, have developed a machine-learning-based CAPTCHA solver that they claim can overcome 94.4% of real challenges on dark websites. The collection of cyber-threat intelligence from illicit dark web markets and forums becomes challenging and expensive, as employees have to be involved in the CAPTCHA solving step.
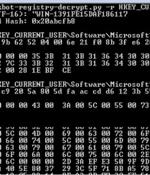
Cybersecurity researchers have decoded the mechanism by which the versatile Qakbot banking trojan handles the insertion of encrypted configuration data into the Windows Registry. Although mainly fashioned as an information-stealing malware, Qakbot has since shifted its goals and acquired new functionality to deliver post-compromise attack platforms such as Cobalt Strike Beacon, with the final objective of loading ransomware on infected machines.
"The confusion in URL parsing can cause unexpected behavior in the software, and could be exploited by threat actors to cause denial-of-service conditions, information leaks, or possibly conduct remote code execution attacks," the researchers said in a report shared with The Hacker News. With URLs being a fundamental mechanism by which resources - located either locally or on the web - can be requested and retrieved, differences in how the parsing libraries interpret a URL request could pose significant risk for users.

Hackers targeted cybersecurity researchers and developers this week in a sophisticated malware campaign distributing a malicious version of the dnSpy. This new campaign was discovered by security researchers 0day enthusiast and MalwareHunterTeam who saw the malicious dnSpy project initially hosted at https://github[.

Cybersecurity researchers have taken the wraps of an organized financial-theft operation undertaken by a discreet actor to target transaction processing systems and siphon funds from entities primarily located in Latin America for at least four years. The malicious hacking group has been codenamed Elephant Beetle by Israeli incident response firm Sygnia, with the intrusions aimed at banks and retail companies by injecting fraudulent transactions among benign activity to slip under the radar after an extensive study of the targets' financial structures.

A persistent denial-of-service vulnerability has been discovered in Apple's iOS mobile operating system that's capable of sending affected devices into a crash or reboot loop upon connecting to an Apple Home-compatible appliance. HomeKit is Apple's software framework that allows iOS and iPadOS users to configure, communicate with, and control connected accessories and smart-home appliances using Apple devices.

Microsoft said it won't be fixing or is pushing patches to a later date for three of the four security flaws uncovered in its Teams business communication platform earlier this March. The disclosure comes from Berlin-based cybersecurity firm Positive Security, which found that the implementation of the link preview feature was susceptible to a number of issues that could "Allow accessing internal Microsoft services, spoofing the link preview, and, for Android users, leaking their IP address, and DoS'ing their Teams app/channels."