Security News
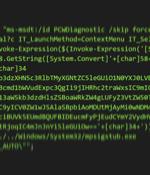
Cybersecurity researchers are calling attention to a zero-day flaw in Microsoft Office that could be abused to achieve arbitrary code execution on affected Windows systems. According to security researcher Kevin Beaumont, who dubbed the flaw "Follina," the maldoc leverages Word's remote template feature to fetch an HTML file from a server, which then makes use of the "Ms-msdt://" URI scheme to run the malicious payload. MSDT is short for Microsoft Support Diagnostics Tool, a utility that's used to troubleshoot and collect diagnostic data for analysis by support professionals to resolve a problem.

A researcher from the Beijing Institute of Tracking and Telecommunications advocated for Chinese military capability to take out Starlink satellites on the grounds of national security in a peer-reviewed domestic journal. According to the South China Morning Post, lead author Ren Yuanzhen and colleagues advocated in Modern Defence Technology not only for China to develop anti-satellite capabilities, but also to have a surveillance system that could monitor and track all satellites in Starlink's constellation.

An unknown advanced persistent threat group has been linked to a series of spear-phishing attacks targeting Russian government entities since the onset of the Russo-Ukrainian war in late February 2022. The cybersecurity company attributed the attacks with low confidence to a Chinese hacking group, citing infrastructure overlaps between the RAT and Sakula Rat malware used by a threat actor known as Deep Panda.

Meta's ad transparency tools will soon reveal another treasure trove of data: advertiser targeting choices for political, election-related, and social issue spots. Meta said it plans to add the targeting data into its Facebook Open Research and Transparency environment for academic researchers at the end of May. The move comes a day after Meta's reputation as a bad data custodian resurfaced with news of a lawsuit filed in Washington DC against CEO Mark Zuckerberg.

Proof-of-concept exploit code is about to be published for a vulnerability that allows administrative access without authentication in several VMware products. Security researchers at attack surface assessment company Horizon3 announced today that they managed to create a working proof-of-concept exploit code for CVE-2022-22972 and will be releasing a technical report shortly.

The policy for the first time directs that good-faith security research should not be charged. Good faith security research means accessing a computer solely for purposes of good-faith testing, investigation, and/or correction of a security flaw or vulnerability, where such activity is carried out in a manner designed to avoid any harm to individuals or the public, and where the information derived from the activity is used primarily to promote the security or safety of the class of devices, machines, or online services to which the accessed computer belongs, or those who use such devices, machines, or online services.

Multiple versions of a WordPress plugin by the name of "School Management Pro" harbored a backdoor that could grant an adversary complete control over vulnerable websites. The backdoor, which is believed to have existed since version 8.9, enables "An unauthenticated attacker to execute arbitrary PHP code on sites with the plugin installed," Jetpack's Harald Eilertsen said in a Friday write-up.

A case of software supply chain attack has been observed in the Rust programming language's crate registry that leveraged typosquatting techniques to publish a rogue library containing malware. Cybersecurity firm SentinelOne dubbed the attack "CrateDepression."

The US Justice Department has directed prosecutors not to charge "Good-faith security researchers" with violating the Computer Fraud and Abuse Act if their reasons for hacking are ethical - things like bug hunting, responsible vulnerability disclosure, or above-board penetration testing. "The Department has never been interested in prosecuting good-faith computer security research as a crime, and today's announcement promotes cybersecurity by providing clarity for good-faith security researchers who root out vulnerabilities for the common good."

The U.S. Department of Justice announced the revision of its policy regarding charging violations of the Computer Fraud and Abuse Act, which says that, among other things, good-faith security researchers will no longer be charged and prosecuted. Good faith security research means accessing a computer solely for purposes of good-faith testing, investigation, and/or correction of a security flaw or vulnerability, where such activity is carried out in a manner designed to avoid any harm to individuals or the public, and where the information derived from the activity is used primarily to promote the security or safety of the class of devices, machines, or online services to which the accessed computer belongs, or those who use such devices, machines, or online services.