Security News

Researchers at firmware and supply-chain security company Ecylpsium claim to have found what they have rather dramtically dubbed a "Backdoor" in hundreds of motherboard models from well-known hardware maker Gigabyte. You can reinstall Windows at any time, and a standard Windows image doesn't know whether you're going to be using a Gigabyte motherboard or not, so it doesn't come with GigabyteUpdateService.

Security researchers have shared a deep dive into the commercial Android spyware called Predator, which is marketed by the Israeli company Intellexa. "A deep dive into both spyware components indicates that Alien is more than just a loader for Predator and actively sets up the low-level capabilities needed for Predator to spy on its victims," Cisco Talos said in a technical report.

Symantec, by Broadcom Software, is tracking the activity under its insect-themed moniker Lancefly, with the attacks making use of a "Powerful" backdoor called Merdoor. "The backdoor is used very selectively, appearing on just a handful of networks and a small number of machines over the years, with its use appearing to be highly targeted," Symantec said in an analysis shared with The Hacker News.

Black Hat Asia Threat groups have infected millions of Androids worldwide with malicious firmware before the devices have even been shipped from their manufacturers, according to Trend Micro researchers at Black Hat Asia. The mainly mobile devices, but also smartwatches, TVs and more, have their manufacturing outsourced to an original equipment manufacturer, a process the researchers say makes them easily infiltrated.

The company's mea culpa came two days after a cyberextortion gang going by the name Money Message claimed to have stolen MSI source code, BIOS development tools, and private keys. Researchers at vulnerability research company Binarly claim not only to have got hold of the data stolen in the breach, but also to have searched through it for embedded crpyotgraphic keys and come up with numerous hits.

The advanced persistent threat actor known as SideWinder has been accused of deploying a backdoor in attacks directed against Pakistan government organizations as part of a campaign that commenced in late November 2022. "In this campaign, the SideWinder advanced persistent threat group used a server-based polymorphism technique to deliver the next stage payload," the BlackBerry Research and Intelligence Team said in a technical report published Monday.

Three new security flaws have been disclosed in Microsoft Azure API Management service that could be abused by malicious actors to gain access to sensitive information or backend services. This includes two server-side request forgery flaws and one instance of unrestricted file upload functionality in the API Management developer portal, according to Israeli cloud security firm Ermetic.
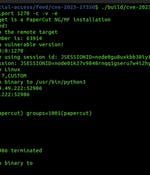
Cybersecurity researchers have found a way to exploit a recently disclosed critical flaw in PaperCut servers in a manner that bypasses all current detections. Tracked as CVE-2023-27350, the issue affects PaperCut MF and NG installations that could be exploited by an unauthenticated attacker to execute arbitrary code with SYSTEM privileges.

The researcher reached out to BleepingComputer stating that by hijacking these packages he hopes to get a job. Yesterday, a researcher with the pseudonym 'neskafe3v1' reached out to BleepingComputer stating he had taken over fourteen Packagist packages, with one of them having over 500 million installs.

Cybersecurity researchers have uncovered weaknesses in a software implementation of the Border Gateway Protocol that could be weaponized to achieve a denial-of-service condition on vulnerable BGP peers. The three vulnerabilities reside in version 8.4 of FRRouting, a popular open source internet routing protocol suite for Linux and Unix platforms.