Security News

Six vulnerabilities have been fixed in the newest versions of Rsync (v3.4.0), two of which could be exploited by a malicious client to achieve arbitrary code execution on a machine with a running...

Threat actors are attempting to take advantage of a recently disclosed security flaw impacting GFI KerioControl firewalls that, if successfully exploited, could allow malicious actors to achieve...
A growing number of enterprises in the US are adopting managed network services to support AI and other new technologies across increasingly complex networks, according to ISG. US enterprises lead...

Chinese state-sponsored threat actors hacked the U.S. Treasury Department after breaching a remote support platform used by the federal agency. [...]
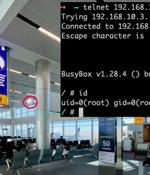
Cybersecurity researchers have discovered several security flaws in the cloud management platform developed by Ruijie Networks that could permit an attacker to take control of the network...

Apache has released a security update that addresses an important vulnerability in Tomcat web server that could lead to an attacker achieving remote code execution. [...]

Sophos has addressed three vulnerabilities in its Sophos Firewall product that could allow remote unauthenticated threat actors to perform SQL injection, remote code execution, and gain privileged...

Sophos has addressed three vulnerabilities in its Sophos Firewall product that could allow remote unauthenticated threat actors to perform SQL injection, remote code execution, and gain privileged...
A now-patched critical security flaw impacting Fortinet FortiClient EMS is being exploited by malicious actors as part of a cyber campaign that installed remote desktop software such as AnyDesk...

Privileged access management company BeyondTrust suffered a cyberattack in early December after threat actors breached some of its Remote Support SaaS instances. [...]