Security News

I am also skeptical that we are going to see useful quantum computers anytime soon. Since at least 2019, I have been saying that this is hard.

The maintainers of the open-source continuous integration/continuous delivery and deployment (CI/CD) automation software Jenkins have resolved nine security flaws, including a critical bug that,...
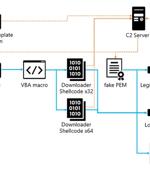
Cybersecurity researchers have uncovered an updated version of a backdoor called LODEINFO that's distributed via spear-phishing attacks. The findings come from Japanese company ITOCHU Cyber &...

The 2023/2024 Axur Threat Landscape Report provides a comprehensive analysis of the latest cyber threats. The information combines data from the platform's surveillance of the Surface, Deep, and...

ESET researchers have discovered NSPX30, a sophisticated implant used by a new China-aligned APT group, which they dubbed Blackwood. It leverages adversary-in-the-middle techniques to hijack update requests from legitimate software to deliver the implant.

All types of cyber threat actor are already using artificial intelligence to varying degrees, UK National Cyber Security Centre's analysts say, and predict that AI "Will almost certainly increase the volume and heighten the impact of cyberattacks over the next two years." Although AI is used by all types of cyber threat actors, it will particularly benefit less-skilled ones, as it will enhance their ability to carry out social engineering attacks and create convincing phishing emails.
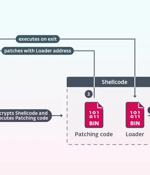
A previously undocumented China-aligned threat actor has been linked to a set of adversary-in-the-middle (AitM) attacks that hijack update requests from legitimate software to deliver a...

A new Go-based malware loader called CherryLoader has been discovered by threat hunters in the wild to deliver additional payloads onto compromised hosts for follow-on exploitation. Arctic Wolf...

Spotting insider threats can be more challenging for a simple reason: insiders already have legitimate access - whether limited or full - to an organization's network, systems, or other assets. "Identifying insider threats is not a binary process. Insiders can be malicious, lack the skills to do their jobs properly, or be victims of coercion. Thus, it is important to understand the different types of insider threats and the vectors that are most applicable to your organization," Mandiant researchers recently noted.

Hackers with links to the Kremlin are suspected to have infiltrated information technology company Hewlett Packard Enterprise's (HPE) cloud email environment to exfiltrate mailbox data. "The...