Security News
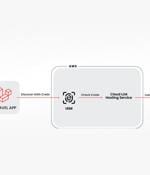
Cybersecurity researchers have discovered a novel attack that employs stolen cloud credentials to target cloud-hosted large language model (LLM) services with the goal of selling access to other...

The thunderstorms of April patches have passed, and it has been pretty calm leading up to May 2024 Patch Tuesday. April 2024 Patch Tuesday turned out to be a busy one with 150 new CVEs addressed by Microsoft.

When experts refer to password protection as a security measure, they typically describe situations where a password is the sole method of accessing data, which usually has built-in protection against hacking, either through software or hardware encryption. Most password protection methods use some form of encryption, but is there a clear choice between software and hardware encryption when it comes to protecting your personal or business files from theft, loss, or hacking?

Cybercriminals are targeting the ever-increasing number of new vulnerabilities resulting from the exponential growth in the number and variety of connected devices and an explosion in new applications and online services, according to Fortinet. Attacks started on average 4.76 days after new exploits were publicly disclosed: Like the 1H 2023 Global Threat Landscape Report, FortiGuard Labs sought to determine how long it takes for a vulnerability to move from initial release to exploitation, whether vulnerabilities with a high Exploit Prediction Scoring System score get exploited faster, and whether it could predict the average time-to-exploitation using EPSS data.

Nmap is a free, open-source tool for network discovery and security auditing. It's valued by systems and network administrators for network inventory, managing service upgrade schedules, and monitoring host or service uptime.

93% of security leaders said public GenAI was in use across their respective organizations, and 91% reported using GenAI specifically for cybersecurity operations, according to Splunk. Cybersecurity leaders are divided on who will gain the upper hand in leveraging GenAI tools: cybersecurity defenders or threat actors.

Document image-of-image was the most prevalent identity document fraud technique in 2023, occurring in 63% of all IDs that were rejected, according to Socure. Document image-of-image occurs when the user takes a photograph or uses a screenshot image of an ID, rather than providing a live capture of the document.

Poland says a state-backed threat group linked to Russia's military intelligence service has been targeting Polish government institutions throughout the week. According to evidence found by CSIRT MON, the country's Computer Security Incident Response Team and CERT Polska, Russian APT28 state hackers attacked multiple government institutions in a large-scale phishing campaign.

Project management platform Monday.com has removed its "Share Update" feature after threat actors abused it in phishing attacks. On Tuesday, Monday.com customers told BleepingComputer they were concerned that the company was compromised after receiving phishing emails from its email accounts.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.