Security News
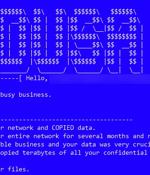
The threat actors associated with the Medusa ransomware have ramped up their activities following the debut of a dedicated data leak site on the dark web in February 2023 to publish sensitive data...

A new analysis of the sophisticated commercial spyware called Predator has revealed that its ability to persist between reboots is offered as an "add-on feature" and that it depends on the...

"Multi-cloud computing offers huge benefits but makes IT far more complex," said Bernie Hoecker, partner, Enterprise Cloud Transformation leader, ISG. "Enterprises that have made the leap are adopting increasingly powerful tools to manage that complexity." Cloud observability platforms are increasingly essential as multi-cloud complexity increases, the report says.

SessionProbe is a multi-threaded pentesting tool designed to evaluate user privileges in web applications. It takes a user's session token and checks for a list of URLs if access is possible, highlighting potential authorization issues.

Phishing attacks are steadily becoming more sophisticated, with cybercriminals investing in new ways of deceiving victims into revealing sensitive information or installing malicious software. One...

Intel has released fixes to close out a high-severity flaw codenamed Reptar that impacts its desktop, mobile, and server CPUs. Tracked as CVE-2023-23583 (CVSS score: 8.8), the issue has the...

Spanish law enforcement officials have announced the arrest of 34 members of a criminal group that carried out various online scams, netting the gang about €3 million ($3.2 million) in illegal...
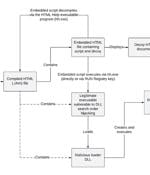
A "multi-year" Chinese state-sponsored cyber espionage campaign has been observed targeting South Korean academic, political, and government organizations. Recorded Future's Insikt Group, which is...

Enterprise application environments consist of geographically distributed and loosely coupled microservices that span multiple cloud and on-premises environments. Users from different locations access them through different devices.

Bruschetta-Board is a device for all hardware hackers looking for a fairly-priced all-in-one debugger and programmer that supports UART, JTAG, I2C & SPI protocols and allows to interact with different targets' voltages. A handy feature of Bruschetta-Board is the fact it mounts level shifters.