Security News

It's the second Tuesday of the month, and Microsoft has released another set of security updates to fix a total of 97 flaws impacting its software, one of which has been actively exploited in ransomware attacks in the wild. "An attacker who successfully exploited this vulnerability could gain SYSTEM privileges," Microsoft said in an advisory, crediting researchers Boris Larin, Genwei Jiang, and Quan Jin for reporting the issue.

It's April 2023 Patch Tuesday, and Microsoft has released fixes for 97 CVE-numbered vulnerabilities, including one actively exploited zero-day. "CVE-2023-28252 is the second CLFS elevation of privilege zero-day exploited in the wild this year and the fourth in the last two years. It is also the second CLFS zero-day disclosed to Microsoft by researchers from Mandiant and DBAPPSecurity, though it is unclear if both of these discoveries are related to the same attacker."

Today is Microsoft's April 2023 Patch Tuesday, and security updates fix one actively exploited zero-day vulnerability and a total of 97 flaws. This count does not include seventeen Microsoft Edge vulnerabilities fixed on April 6th. One zero-day fixed.
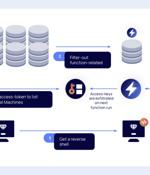
A "By-design flaw" uncovered in Microsoft Azure could be exploited by attackers to gain access to storage accounts, move laterally in the environment, and even execute remote code. "It is possible to abuse and leverage Microsoft Storage Accounts by manipulating Azure Functions to steal access-tokens of higher privilege identities, move laterally, potentially access critical business assets, and execute remote code," Orca said in a new report shared with The Hacker News.

Microsoft and Fortra are taking legal and technical actions to thwart cyber-criminals from using the latter company's Cobalt Strike software to distribute malware. The US District Court for the Eastern District of New York on March 31 issued a court order allowing Microsoft and Fortra to take down IP addresses that are hosting cracked versions of Cobalt Strike and seize the domain names.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.

Microsoft announced today that Client Access Rules deprecation in Exchange Online will be delayed by one year until September 2024. Microsoft 365 administrators can utilize CARs comprising priority values, exceptions, actions, and conditions to filter client access to Exchange Online using various factors.

We and our store and/or access information on a device, such as cookies and process personal data, such as unique identifiers and standard information sent by a device for personalised ads and content, ad and content measurement, and audience insights, as well as to develop and improve products. With your permission we and our partners may use precise geolocation data and identification through device scanning.
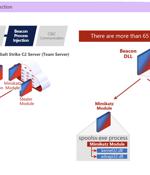
Microsoft said it teamed up with Fortra and Health Information Sharing and Analysis Center to tackle the abuse of Cobalt Strike by cybercriminals to distribute malware, including ransomware. While Cobalt Strike, developed and maintained by Fortra, is a legitimate post-exploitation tool used for adversary simulation, illegal cracked versions of the software have been weaponized by threat actors over the years.

"Customers who contact Microsoft Support after this date will be directed to update their device to the latest version of Windows 10 or upgrade to Windows 11 to remain supported." You can find more details regarding Windows end-of-service dates in the Windows Lifecycle FAQ, the Windows 10 Servicing Frequently Asked Questions, and with the help of the Lifecycle Policy search tool.