Security News

Russian state-backed hacking group Forest Blizzard has been using a known Microsoft Outlook vulnerability to target public and private entities in Poland, Polish Cyber Command has warned. The attacks were further analyzed by Polish Cyber Command, who confirmed that the threat actors have been gaining access to email accounts within Microsoft Exchange servers and modifying folder permissions within the victim's mailbox.

Microsoft's Threat Intelligence team issued a warning earlier today about the Russian state-sponsored actor APT28 actively exploiting the CVE-2023-23397 Outlook flaw to hijack Microsoft Exchange accounts and steal sensitive information. The tech giant also highlighted the exploitation of other vulnerabilities with publicly available exploits in the same attacks, including CVE-2023-38831 in WinRAR and CVE-2021-40444 in Windows MSHTML. Outlook flaw exploitation background.

A previously unknown cyber espionage hacking group named 'AeroBlade' was discovered targeting organizations in the United States aerospace sector. The first attacks attributed to AeroBlade occurred in September 2022, using phishing emails with a document attachment that employs remote template injection to download the second-stage DOTM file.

North Korean-backed state hackers have stolen an estimated $3 billion in a long string of hacks targeting the cryptocurrency industry over the last six years since January 2017. "Since 2017, North Korea has significantly increased its focus on the cryptocurrency industry, stealing an estimated $3 billion worth of cryptocurrency," Recorded Future analysts said.

A Russian national has been found guilty in connection with his role in developing and deploying a malware known as TrickBot, the U.S. Department of Justice (DoJ) announced. Vladimir Dunaev, 40,...

A novel malware named 'Agent Raccoon' is being used in cyberattacks against organizations in the United States, the Middle East, and Africa. Agent Raccoon is a.NET malware disguised as a Google Update or Microsoft OneDrive Updater that leverages the DNS protocol to establish a covert communication channel with the attackers' C2 infrastructure.
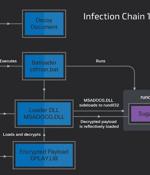
A suspected Chinese-speaking threat actor has been attributed to a malicious campaign that targets the Uzbekistan Ministry of Foreign Affairs and South Korean users with a remote access trojan...

The U.S. Department of the Treasury's Office of Foreign Assets Control (OFAC) on Thursday sanctioned the North Korea-linked adversarial collective known as Kimsuky as well as eight foreign-based...

The U.S. Treasury Department on Wednesday imposed sanctions against Sinbad, a virtual currency mixer that has been put to use by the North Korea-linked Lazarus Group to launder ill-gotten...

CISA is warning that threat actors breached a U.S. water facility by hacking into Unitronics programmable logic controllers exposed online. PLCs are crucial control and management devices in industrial settings, and hackers compromising them could have severe repercussions, such as water supply contamination through manipulating the device to alter chemical dosing.