Security News

Windows 11 will no longer add SMB1 Windows Defender Firewall rules when creating new SMB shares starting with today's Canary Channel Insider Preview Build 25992 build. Before this change and since Windows XP SP2, creating SMB shares set up firewall rules automatically within the "File and Printer Sharing" group for the specified firewall profiles.
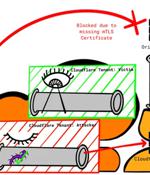
Firewall and distributed denial-of-service (DDoS) attack prevention mechanisms in Cloudflare can be circumvented by exploiting gaps in cross-tenant security controls, defeating the very purpose of...
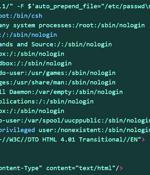
New research has found that close to 12,000 internet-exposed Juniper firewall devices are vulnerable to a recently disclosed remote code execution flaw. VulnCheck, which discovered a new exploit for CVE-2023-36845, said it could be exploited by an "Unauthenticated and remote attacker to execute arbitrary code on Juniper firewalls without creating a file on the system."

About 79 percent of public-facing Juniper SRX firewalls remain vulnerable to a single security flaw can allow an unauthenticated attacker to remotely execute code on the devices, according to threat intelligence platform provider VulnCheck. Juniper revealed and addressed five flaws, which affect all versions of Junos OS on SRX firewalls and EX Series switches, in an out-of-cycle security bulletin on August 17.

What does optimal software security analysis look like?In this Help Net Security interview, Kevin Valk, co-CEO at Codean, discusses the consequences of relying solely on automated tools for software security. Apple offers security researchers specialized iPhones to tinker withApple is inviting security researchers to apply for its Security Research Device Program again, to discover vulnerabilities and earn bug bounties.

Recently disclosed security flaws impacting Juniper firewalls, Openfire, and Apache RocketMQ servers have come under active exploitation in the wild, according to multiple reports. "This flaw allows an unauthorized user to exploit the unauthenticated Openfire Setup Environment within an established Openfire configuration," cloud security firm Aqua said.

Proof-of-concept exploit code has been publicly released for vulnerabilities in Juniper SRX firewalls that, when chained, can allow unauthenticated attackers to gain remote code execution in Juniper's JunOS on unpatched devices.Juniper disclosed four medium-severity bugs in its EX switches and SRX firewalls and released security patches two weeks ago.

Researchers have released additional details about the recently patched four vulnerabilities affecting Juniper Networks' SRX firewalls and EX switches that could allow remote code execution, as well as a proof-of-concept exploit. Earlier this month, Juniper Networks published an out-of-cycle security bulletin notifying customers using its SRX firewalls and EX switches of vulnerabilities that, chained together, would allow attackers to remotely execute code on vulnerable appliances.

Juniper Networks has fixed four vulnerabilities in Junos OS that, if chained together, could allow attackers to achieve remote code execution on the company's SRX firewalls and EX switches.Junos OS is an operating system based on Linux and FreeBSD that runs on Juniper Networks firewalls, network switches and other security devices.

TechRepublic Premium Checklist: How to Create a Team Charter A good team charter should define the purpose of a team, how work will get done and the expected outcomes. Often, a team charter is described as a "Roadmap" for the team and its sponsors.