Security News
Threat actors are leveraging known flaws in Sunlogin software to deploy the Sliver command-and-control framework for carrying out post-exploitation activities. The findings come from AhnLab Security Emergency response Center, which found that security vulnerabilities in Sunlogin, a remote desktop program developed in China, are being abused to deploy a wide range of payloads.

Exploit code has been released for an actively exploited zero-day vulnerability affecting Internet-exposed GoAnywhere MFT administrator consoles. GoAnywhere MFT is a web-based and managed file transfer tool designed to help organizations to transfer files securely with partners and keep audit logs of who accessed the shared files.

A new intelligence gathering campaign linked to the prolific North Korean state-sponsored Lazarus Group leveraged known security flaws in unpatched Zimbra devices to compromise victim systems. Targets of the malicious operation included a healthcare research organization in India, the chemical engineering department of a leading research university, as well as a manufacturer of technology used in the energy, research, defense, and healthcare sectors, suggesting an attempt to breach the supply chain.

A new exploit has been devised to "Unenroll" enterprise- or school-managed Chromebooks from administrative control. Enrolling ChromeOS devices makes it possible to enforce device policies as set by the organization via the Google Admin console, including the features that are available to users.

A new exploit called 'Sh1mmer' allows users to unenroll an enterprise-managed Chromebook, enabling them to install any apps they wish and bypass device restrictions. To bypass these restrictions, security researchers from the Mercury Workshop Team have developed a new exploit called 'Shady Hacking 1nstrument Makes Machine Enrollment Retreat', or 'Sh1mmer,' that lets users unenroll their Chromebooks from enterprise management.

Horizon3 security researchers have released proof-of-concept code for a VMware vRealize Log Insight vulnerability chain that allows attackers to gain remote code execution on unpatched appliances. Earlier today, Horizon3 published the PoC exploit and explained that the RCE exploit "Abuses the various Thrift RPC endpoints to achieve an arbitrary file write."

Users of enterprise-managed Chromebooks now, for better or worse, have a way to break the shackles of administrative control through an exploit called SHI1MMER. SH1MMER - you may pronounce the "1" as an "i" - is a shim exploit, or more specifically, a weaponized Return Merchandise Authorization shim. A shim is Google-signed software used by hardware service vendors for Chromebook diagnostics and repairs.

Security researchers with Horizon3's Attack Team will release an exploit targeting a vulnerability chain next week for gaining remote code execution on unpatched VMware vRealize Log Insight appliances. Now known as VMware Aria Operations for Logs, vRealize Log Insight makes it easier for VMware admins to analyze and manage terabytes of infrastructure and application logs.
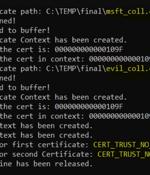
Proof-of-concept (Poc) code has been released for a now-patched high-severity security flaw in the Windows CryptoAPI that the U.S. National Security Agency (NSA) and the U.K. National Cyber...

Akamai researchers have published a PoC exploit for a critical vulnerability in Windows CryptoAPI, which validates public key certificates. "An attacker could manipulate an existing public x.509 certificate to spoof their identity and perform actions such as authentication or code signing as the targeted certificate," Microsoft said in October 2022, when they announced fixes for vulnerable Windows and Windows Server versions.