Security News

Attackers are developing and deploying exploits faster than ever. 56% of the vulnerabilities were exploited within seven days of public disclosure - a 12% rise over 2021 and an 87% rise over 2020.
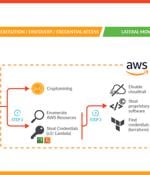
A sophisticated attack campaign dubbed SCARLETEEL is targeting containerized environments to perpetrate theft of proprietary data and software. "The attacker exploited a containerized workload and then leveraged it to perform privilege escalation into an AWS account in order to steal proprietary software and credentials," Sysdig said in a new report.
The RIG exploit kit touched an all-time high successful exploitation rate of nearly 30% in 2022, new findings reveal. Exploit kits are programs used to distribute malware to large numbers of victims by taking advantage of known security flaws in commonly-used software such as web browsers.

The RIG Exploit Kit is undergoing its most successful period, attempting roughly 2,000 intrusions daily and succeeding in about 30% of cases, the highest ratio in the service's long operational history. The RIG exploit kit is a set of malicious JavaScript scripts embedded in compromised or malicious websites by the threat actors, which are then promoted through malvertising.

Threat actors are targeting Internet-exposed Fortinet appliances with exploits targeting CVE-2022-39952, an unauthenticated file path manipulation vulnerability in the FortiNAC webserver that can be abused for remote command execution. These attacks come one day after Horizon3 security researchers released proof-of-concept exploit code for the critical-severity flaw that will add a cron job to initiate a reverse shell on compromised systems as the root user.

Security researchers have released a proof-of-concept exploit for a critical-severity vulnerability in Fortinet's FortiNAC network access control suite. Proof-of-concept exploit code is also available from the company's repository on GitHub.

Security researchers have released a proof-of-concept exploit for a critical-severity vulnerability in Fortinet's FortiNAC network access control suite. Proof-of-concept exploit code is also available from the company's repository on GitHub.

Horizon3's Attack Team has released a PoC exploit for CVE-2022-39952, a critical vulnerability affecting FortiNAC, Fortinet's network access control solution. "Similar to the weaponization of previous archive vulnerability issues that allow arbitrary file write, we use this vulnerability to write a cron job to /etc/cron.d/payload. This cron job gets triggered every minute and initiates a reverse shell to the attacker," shared Zach Hanley, Chief Attack Engineer at Horizon3.

Cybercriminals remained active in spying and information stealing, with lottery-themed adware campaigns used as a tactic to obtain people's contact details, according to Avast. "At the end of 2022, we have seen an increase in human-centered threats, such as scams tricking people into thinking their computer is infected, or that they have been charged for goods they didn't order. It's human nature to react to urgency, fear and try to regain control of issues, and that's where cybercriminals succeed," said Jakub Kroustek, Avast Malware Research Director.

Between July-December 2022, the median open rate for text-based business email compromise attacks was nearly 28%, according to Abnormal Security. "Human beings are relatively easy to manipulate, and employers' expectations regarding the ability of the average employee to identify these modern attacks are far too high. It is much safer to prevent a threat from reaching an employee's inbox than to rely on them to try to detect these sophisticated attacks on their own," Hassold continued.