Security News
The China-linked advanced persistent threat (APT) group known as Mustang Panda has been observed weaponizing Visual Studio Code software as part of espionage operations targeting government...

I asked for a calm August 2024 Patch Tuesday in last month’s forecast article and that came to pass. The updates released were limited to the regular operating systems and all forms of Office...

Cisco has fixed a command injection vulnerability in the Identity Services Engine (ISE) with public exploit code that lets attackers escalate privileges to root on vulnerable systems. [...]
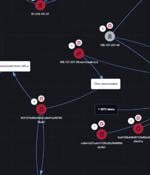
A hacktivist group known as Head Mare has been linked to cyber attacks that exclusively target organizations located in Russia and Belarus. "Head Mare uses more up-to-date methods for obtaining...

Here’s an overview of some of last week’s most interesting news, articles, interviews and videos: SonicWall patches critical flaw affecting its firewalls (CVE-2024-40766) SonicWall has patched a...

A recently patched security flaw in Google Chrome and other Chromium web browsers was exploited as a zero-day by North Korean actors in a campaign designed to deliver the FudModule rootkit. The...

North Korean hackers have exploited a recently patched Google Chrome zero-day (CVE-2024-7971) to deploy the FudModule rootkit after gaining SYSTEM privileges using a Windows Kernel exploit. [...]

Cybersecurity researchers have uncovered a novel malware campaign that leverages Google Sheets as a command-and-control (C2) mechanism. The activity, detected by Proofpoint starting August 5,...

Threat actors are abusing Microsoft Sway to host QR Code phishing campaigns.

Google researchers note similarities, can't find smoking-gun link Google's Threat Analysis Group (TAG) has spotted an interesting pattern: A Kremlin-linked cyber-espionage crew and commercial...