Security News

Nine VSCode extensions on Microsoft's Visual Studio Code Marketplace pose as legitimate development tools while infecting users with the XMRig cryptominer to mine Ethereum and Monero. [...]

Internet service providers (ISPs) in China and the West Coast of the United States have become the target of a mass exploitation campaign that deploys information stealers and cryptocurrency...

A recently disclosed critical security flaw impacting the Aviatrix Controller cloud networking platform has come under active exploitation in the wild to deploy backdoors and cryptocurrency...

Cybersecurity company CrowdStrike is alerting of a phishing campaign that exploits its own branding to distribute a cryptocurrency miner that's disguised as an employee CRM application as part of...

CrowdStrike is warning that a phishing campaign is impersonating the cybersecurity company in fake job offer emails to trick targets into infecting themselves with a Monero cryptocurrency miner...

The popular Ultralytics YOLO11 AI model was compromised in a supply chain attack to deploy cryptominers on devices running versions 8.3.41 and 8.3.42 from the Python Package Index (PyPI) [...]
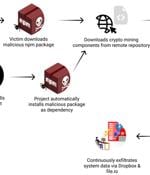
Cybersecurity researchers have discovered a software supply chain attack that has remained active for over a year on the npm package registry by starting off as an innocuous library and later...

The U.S. Department of Justice has announced the arrest and indictment of Charles O. Parks III, known as "CP3O," for allegedly renting large numbers of cloud servers to conduct crypto mining and then skipping out on paying the bills. The DOJ explains that the defendant created a unique scheme that utilized $3.5 million worth of cloud computing resources to mine $970,000 worth of cryptocurrency at the expense of two cloud service providers.

Cybersecurity researchers have identified a new attack that exploits misconfigurations in Apache Hadoop and Flink to deploy cryptocurrency miners within targeted environments. "This attack is...
Three new malicious packages have been discovered in the Python Package Index (PyPI) open-source repository with capabilities to deploy a cryptocurrency miner on affected Linux devices. The three...