Security News

Members of the Five Eyes intelligence alliance warned today that APT29 Russian Foreign Intelligence Service hackers are now switching to attacks targeting their victims' cloud services. The Russian cyberspies also compromised Microsoft 365 accounts belonging to various entities within NATO nations to obtain foreign policy-related data and targeted governments, embassies, and senior officials throughout Europe associated in a string of phishing attacks.
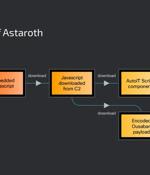
Cybersecurity researchers are warning about a spike in email phishing campaigns that are weaponizing the Google Cloud Run service to deliver various banking trojans such as Astaroth (aka...

Webinar Dealing with the double trouble of relentless cyber threats and regular technology refresh cycles can stretch already overworked security practitioners. Multi cloud might bring flexibility, but it can also increase the risk of misconfiguration and malicious attacks for example.

After select US federal agencies tested Microsoft's expanded cloud logging capabilities for six months, Microsoft is now making them available to all agencies using Microsoft Purview Audit - regardless of license tier. Microsoft first announced the expanded cloud logging capabilities in July 2023, after it revealed that Chinese hackers accessed email accounts belonging to 25 organizations and government agencies.

Over 29% of IT leaders found that moving projects from on-premises to the cloud was more expensive than expected, while 65% said it was financially predictable. The cost-benefit analysis of cloud versus on-premises infrastructure varies greatly depending on the organization.

Security researchers are warning of hackers abusing the Google Cloud Run service to distribute massive volumes of banking trojans like Astaroth, Mekotio, and Ousaban. Google Cloud Run is lets users deploy frontend and backend services, websites or applications, handle workloads without the effort of managing an infrastructure or scaling.

As senior director and global head of the office of the chief information security officer at Google Cloud, Nick Godfrey oversees educating employees on cybersecurity as well as handling threat detection and mitigation. We conducted an interview with Godfrey via video call about how CISOs and other tech-focused business leaders can allocate their finite resources, getting buy-in on security from other stakeholders, and the new challenges and opportunities introduced by generative AI. Since Godfrey is based in the United Kingdom, we asked his perspective on UK-specific considerations as well.

Cloud computing has innovated how organizations operate and manage IT operations, such as data storage, application deployment, networking, and overall resource management. The cloud offers...

According to recent surveys, 98% of organizations keep their financial, business, customer and/or employee information in the cloud but, at the same time, 95% of cloud security professionals are not sure their security protections and their team would manage to detect and respond to security threats or incidents affecting their cloud infrastructure. Cloud misconfiguration errors may grant attackers unauthorized access to system functions and sensitive data, and have the potential to harm the integrity and security of the organization's cloud.

Prowler is an open-source security tool designed to assess, audit, and enhance the security of AWS, GCP, and Azure. "Easy to use from the command line with simple, understandable output, Prowler offers standard reporting formats like CSV and JSON, enabling users to thoroughly examine findings across any cloud provider, all in a uniform format. Its seamless integrations with Security Hub and S3 facilitate easy incorporation with other SIEMs, databases, and more. The ability to write custom checks and develop custom security frameworks is crucial for our expanding community," Toni de la Fuente, the creator of Prowler, told Help Net Security.