Security News
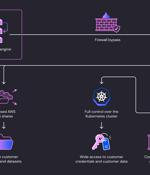
Cybersecurity researchers have uncovered security shortcomings in SAP AI Core cloud-based platform for creating and deploying predictive artificial intelligence workflows that could be exploited to get hold of access tokens and customer data. "The vulnerabilities we found could have allowed attackers to access customers' data and contaminate internal artifacts - spreading to related services and other customers' environments," security researcher Hillai Ben-Sasson said in a report shared with The Hacker News.

Unknown threat actors have been observed leveraging open-source tools as part of a suspected cyber espionage campaign targeting global government and private sector organizations. Recorded Future's Insikt Group is tracking the activity under the temporary moniker TAG-100, noting that the adversary likely compromised organizations in at least ten countries across Africa, Asia, North America, South America, and Oceania, including two unnamed Asia-Pacific intergovernmental organizations.

The infamous cybercrime group known as Scattered Spider has incorporated ransomware strains such as RansomHub and Qilin into its arsenal, Microsoft has revealed. Scattered Spider is the...

Threat actors are actively exploiting a recently disclosed critical security flaw impacting Apache HugeGraph-Server that could lead to remote code execution attacks. It has been described as a remote command execution flaw in the Gremlin graph traversal language API. "Users are recommended to upgrade to version 1.3.0 with Java11 and enable the Auth system, which fixes the issue," the Apache Software Foundation noted in late April 2024.

CISA is warning that a critical GeoServer GeoTools remote code execution flaw tracked as CVE-2024-36401 is being actively exploited in attacks. On June 30th, GeoServer disclosed a critical 9.8 severity remote code execution vulnerability in its GeoTools plugin caused by unsafely evaluating property names as XPath expressions.

Microsoft says the Scattered Spider cybercrime gang has added Qilin ransomware to its arsenal and is now using it in attacks. "In the second quarter of 2024, financially motivated threat actor Octo Tempest, our most closely tracked ransomware threat actor, added RansomHub and Qilin to its ransomware payloads in campaigns," Microsoft said Monday.

The zero-day exploit used to leverage CVE-2024-38112, a recently patched Windows MSHTML vulnerability, was wielded by an APT group dubbed Void Banshee to deliver malware to targets in North America, Europe, and Southeast Asia, threat hunters with Trend Micro's Zero Day Initiative have shared. As previously explained by Check Point researcher Haifei Li, the attackers used files that were specially crafted to exploit the vulnerability but were made to look like PDFs. "The threat actor leveraged CVE-2024-38112 to execute malicious code by abusing the MHTML protocol handler and x-usc directives through internet shortcut files. Using this technique, the threat actor was able to access and run files directly through the disabled Internet Explorer instance on Windows machines," Trend Micro researchers noted.
The Iranian nation-state actor known as MuddyWater has been observed using a never-before-seen backdoor as part of a recent attack campaign, shifting away from its well-known tactic of deploying legitimate remote monitoring and management software for maintaining persistent access. "Compared to previous campaigns, this time MuddyWater changed their infection chain and did not rely on the legitimate Atera remote monitoring and management tool as a validator," Sekoia said in a report shared with The Hacker News.

The Iranian-backed MuddyWatter hacking group has partially switched to using a new custom-tailored malware implant to steal files and run commands on compromised systems. "We discovered several versions of the malware being distributed, with differences between each version showing improvements and bug fixes," Check Point said.
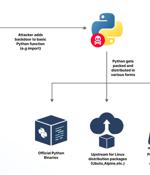
Cybersecurity researchers said they discovered an accidentally leaked GitHub token that could have granted elevated access to the GitHub repositories of the Python language, Python Package Index, and the Python Software Foundation repositories. JFrog, which found the GitHub Personal Access Token, said the secret was leaked in a public Docker container hosted on Docker Hub.