Security News

A new politically-motivated hacker group named "Moses Staff" has been linked to a wave of targeted attacks targeting Israeli organizations since September 2021 with the goal of plundering and leaking sensitive information prior to encrypting their networks, with no option to regain access or negotiate a ransom. "The group openly states that their motivation in attacking Israeli companies is to cause damage by leaking the stolen sensitive data and encrypting the victim's networks, with no ransom demand," Check Point Research said in a report published Monday.

A new wave of attacks starting late last week has hacked close to 300 WordPress sites to display fake encryption notices, trying to trick the site owners into paying 0.1 bitcoin for restoration. The researchers discovered that the websites had not been encrypted, but rather the threat actors modified an installed WordPress plugin to display a ransom note and countdown when.

Cybersecurity researchers have demonstrated yet another variation of the Rowhammer attack affecting all DRAM chips that bypasses currently deployed mitigations, thereby effectively compromising the security of the devices. Originally disclosed in 2014, Rowhammer refers to a fundamental hardware vulnerability that could be abused to alter or corrupt memory contents by taking advantage of DRAM's tightly-packed, matrix-like memory cell architecture to repeatedly access certain rows that induces an electrical disturbance large enough to cause the capacitors in neighbouring rows to leak charge faster and flip bits stored in the "Victim" rows adjacent to them.

Boffins at ETH Zurich, Vrije Universiteit Amsterdam, and Qualcomm Technologies have found that varying the order, regularity, and intensity of rowhammer attacks on memory chips can defeat defenses, thereby compromising security on any device with DRAM. The vulnerability, tracked as CVE-2021-42114 with a severity of 9 out of 10, means that pretty much any shared workload on physical hardware is potentially susceptible to a rowhammer attack, even if the device in question relies on a memory defense known as Target Row Refresh. Around 2014 [PDF], computer researchers associated with Carnegie Mellon and Intel revealed that by "Hammering" RAM chips with write operations, they could flip bits stored in adjacent memory rows, creating errors that can be exploited to gain access to kernel memory, to elevate privileges, and to break the isolation between virtual machines and the host.
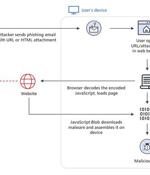
Threat actors are increasingly banking on the technique of HTML smuggling in phishing campaigns as a means to gain initial access and deploy an array of threats, including banking malware, remote administration trojans, and ransomware payloads. HTML smuggling is an approach that allows an attacker to "Smuggle" first-stage droppers, often encoded malicious scripts embedded within specially-crafted HTML attachment or web pages, on a victim machine by taking advantage of basic features in HTML5 and JavaScript rather than exploiting a vulnerability or a design flaw in modern web browsers.

Researchers uncovered a vulnerability in Intel Processors that could affect laptops, cars and embedded systems. The flaw enables testing or debugging modes on multiple Intel processor lines, which could allow an unauthorized user with physical access to obtain enhanced privileges on the system.

Learn how to detect phishing on LinkedIn and protect yourself from it. Abusing LinkedIn is one of those techniques that is very effective because a lot of professionals use and depend on LinkedIn for their activities or work relationships.
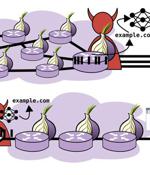
A new analysis of website fingerprinting attacks aimed at the Tor web browser has revealed that it's possible for an adversary to glean a website frequented by a victim, but only in scenarios where the threat actor is interested in a specific subset of the websites visited by users. Tor browser offers "Unlinkable communication" to its users by routing internet traffic through an overlay network, consisting of more than six thousand relays, with the goal of anonymizing the originating location and usage from third parties conducting network surveillance or traffic analysis.

Armis released data showing the increased security risk faced by healthcare organizations and patients as an increase in connected devices creates an expanded attack surface, putting the patient journey at risk. The pitfalls of an expanded attack surface for healthcare organizations Increased cyber risk: 85% of IT professional respondents agreed they have seen increased cyber risk over the past 12 months.

Microsoft has seen a surge in malware campaigns using HTML smuggling to distribute banking malware and remote access trojans. While HTML smuggling is not a new technique, Microsoft is seeing it increasingly used by threat actors to evade detection, including the Nobelium hacking group behind the SolarWinds attacks.