Security News

The U.S. Cybersecurity and Infrastructure Security Agency has added a recently patched critical security flaw in Zyxel gear to its Known Exploited Vulnerabilities catalog, citing evidence of active exploitation. Federal agencies in the U.S. are mandated to update their devices by June 21, 2023.

Hackers are performing widespread exploitation of a critical-severity command injection flaw in Zyxel networking devices, tracked as CVE-2023-28771, to install malware. The flaw, which is present in the default configuration of impacted firewall and VPN devices, can be exploited to perform unauthenticated remote code execution using a specially crafted IKEv2 packet to UDP port 500 on the device.
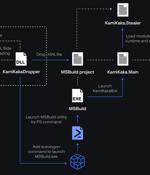
The threat actor known as Dark Pink has been linked to five new attacks aimed at various entities in Belgium, Brunei, Indonesia, Thailand, and Vietnam between February 2022 and April 2023. Dark Pink, also called Saaiwc Group, is an advanced persistent threat actor believed to be of Asia-Pacific origin, with attacks targeting entities primarily located in East Asia and, to a lesser extent, in Europe.

The threat actors behind RomCom RAT are leveraging a network of fake websites advertising rogue versions of popular software at least since July 2022 to infiltrate targets. The remote access trojan has since been used heavily in attacks targeting Ukrainian state bodies and military systems via spoofed versions of legitimate software.

Just days after releasing the second - and supposedly more stable and secure - version of its decentralized finance app, Jimbos Protocol over the weekend was hit by attackers who stole stole 4,090 ETH tokens from the project worth about $7.5 million. The developers behind the Arbitrum-based app were the apparent victims of a flash loan attack and now are scrambling to track down the light-fingered coders and retrieve the lost funds.

Threat actors are abusing generative AI to carry out child sex abuse material, disinformation, fraud and extremism, according to ActiveFence. Key ways to abuse generative AI:. CSAM. Researchers tracked a 172% increase in the volume of shared CSAM produced by generative AI in the first quarter of this year.

Jimbos Protocol, an Arbitrum-based DeFi project, has suffered a flash loan attack that resulted in the loss of more than of 4000 ETH tokens, currently valued at over $7,500,000. According to blockchain security experts at PeckShield, Jimbos Protocol was the victim of a flash loan attack that leveraged the lack of slippage control on the platform.
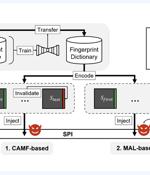
Researchers have discovered an inexpensive attack technique that could be leveraged to brute-force fingerprints on smartphones to bypass user authentication and seize control of the devices. The approach, dubbed BrutePrint, bypasses limits put in place to counter failed biometric authentication attempts by weaponizing two zero-day vulnerabilities in the smartphone fingerprint authentication framework.

Managed Care of North America Dental has published a data breach notification on its website, informing almost 9 million patients that their personal data were compromised.MCNA Dental is one of the largest government-sponsored dental care and oral health insurance providers in the U.S. In a notice published Friday, MCNA says it became aware of unauthorized access to its computer systems on March 6th, 2023, with an investigation revealing that the hackers first gained access to MCNA's network on February 26th, 2023.

A crypter malware dubbed AceCryptor has been used to pack numerous strains of malware since 2016. Some of the prominent malware families contained within AceCryptor are SmokeLoader, RedLine Stealer, RanumBot, Raccoon Stealer, Stop ransomware, and Amadey, among others.