Security News

Adobe warns that a critical ColdFusion pre-authentication remote code execution vulnerability tracked as CVE-2023-29300 is actively exploited in attacks. CVE-2023-29300 is rated as critical with a 9.8 severity rating, as it can be used by unauthenticated visitors to remotely execute commands on vulnerable Coldfusion 2018, 2021, and 2023 servers in low-complexity attacks.

Adobe warns that a critical ColdFusion pre-authentication remote code execution vulnerability tracked as CVE-2023-29300 is actively exploited in attacks.CVE-2023-29300 is rated as critical with a 9.8 severity rating, as it can be used by unauthenticated visitors to remotely execute commands on vulnerable Coldfusion 2018, 2021, and 2023 servers in low-complexity attacks.

For anyone ready to find an attack surface management vendor, review these six questions before getting started to understand the key features to look for in an ASM platform and the qualities of the vendor who supports it. Does your platform have the capability to discover the unknown? How do you prevent alert fatigue, prioritize alerts and remove false positives? Can you track attack surface changes over time? How do you plan to evolve the platform going forward? What services related to ASM do you offer? Can we demo or test run the platform?

Quantum computing is poised to revolutionize the way we secure and privatize data. It can potentially disrupt our existing encryption methods, endangering sensitive data from various sources in ways even beyond what we've experienced with AI. In this Help Net Security video, Tommaso Gagliardoni, Global Practice Lead in Quantum Security at Kudelski Security, discusses quantum-based attacks.
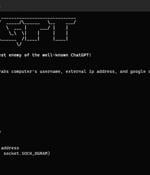
According to findings from SlashNext, a new generative AI cybercrime tool called WormGPT has been advertised on underground forums as a way for adversaries to launch sophisticated phishing and business email compromise attacks.In the hands of a bad actor, tools like WormGPT could be a powerful weapon, especially as OpenAI ChatGPT and Google Bard are increasingly taking steps to combat the abuse of large language models to fabricate convincing phishing emails and generate malicious code.

Over the last few months, Clop ransomware gang has been exploiting a vulnerability in the MOVEit File Transfer utility to breach hundreds of companies to steal their data and attempt extortion against them. This week, Clop ransomware gang published Shutterfly's name on its data leak site, among other companies it has targeted, largely via the MOVEit SQL Injection vulnerability, tracked as CVE-2023-34362.

Zimbra urged admins today to manually fix a zero-day vulnerability actively exploited to target and compromise Zimbra Collaboration Suite email servers."A security vulnerability in Zimbra Collaboration Suite Version 8.8.15 that could potentially impact the confidentiality and integrity of your data has surfaced. [.] The fix is planned to be delivered in the July patch release," the company warned on Thursday via an advisory that doesn't inform customers the bug is also being abused in the wild.
Government entities, military organizations, and civilian users in Ukraine and Poland have been targeted as part of a series of campaigns designed to steal sensitive data and gain persistent remote access to the infected systems. The intrusion set, which stretches from April 2022 to July 2023, leverages phishing lures and decoy documents to deploy a downloader malware called PicassoLoader, which acts as a conduit to launch Cobalt Strike Beacon and njRAT. "The attacks used a multistage infection chain initiated with malicious Microsoft Office documents, most commonly using Microsoft Excel and PowerPoint file formats," Cisco Talos researcher Vanja Svajcer said in a new report.
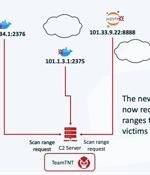
As many as 196 hosts have been infected as part of an aggressive cloud campaign mounted by the TeamTNT group called Silentbob. "The botnet run by TeamTNT has set its sights on Docker and Kubernetes environments, Redis servers, Postgres databases, Hadoop clusters, Tomcat and Nginx servers, Weave Scope, SSH, and Jupyter applications," Aqua security researchers Ofek Itach and Assaf Morag said in a report shared with The Hacker News.

The U.S. Cybersecurity and Infrastructure Security Agency has alerted of two security flaws impacting Rockwell Automation ControlLogix EtherNet/IP communication module models that could be exploited to achieve remote code execution and denial-of-service. "The results and impact of exploiting these vulnerabilities vary depending on the ControlLogix system configuration, but they could lead to denial or loss of control, denial or loss of view, theft of operational data, or manipulation of control for disruptive or destructive consequences on the industrial process for which the ControlLogix system is responsible," Draogos said.