Security News > 2024 > March

The U.S. Treasury Department has sanctioned a Wuhan-based company used by the Chinese Ministry of State Security as cover in attacks against U.S. critical infrastructure organizations. The Office of Foreign Assets Control has also designated two Chinese nationals linked to the APT31 Chinese state-backed hacking group and who worked as contractors for the Wuhan Xiaoruizhi Science and Technology Company, Limited MSS front company for their involvement in the same attacks and "Endangering U.S. national security."

Academic researchers developed ZenHammer, the first variant of the Rowhammer DRAM attack that works on CPUs based on recent AMD Zen microarchitecture that map physical addresses on DDR4 and DDR5 memory chips. The ZenHammer attack was developed by researchers at public research university ETH Zurich, who shared their technical paper with BleepingComputer.

When you think of virtual private networks, chances are pretty good your thoughts go to the tried and true VPNs of old, which made it possible for you to securely connect to your company network such that your local computer behaved as if it were within the company LAN. This concise guide, written by Jack Wallen for TechRepublic Premium, looks at something different - mobile VPNs and why you need them, how they work and what you should look for in a VPN service. You might be at home, or you might be working on a coffee shop wireless network.

In what was originally being called a serious IT outage at the end of last week, the union confirmed to The Register today that the incident is now being treated as an attack, the full extent of which is still being assessed. The CWU told us on March 22 that its email services weren't working and that it has engaged third-party cybersecurity experts who have been on site since 0900 UTC on March 21.

Users may have to upgrade twice to protect their browsers Mozilla has swiftly patched a pair of critical Firefox zero-days after a researcher debuted them at a Vancouver cybersec competition.…

The GoFetch vulnerability found on Apple M-series and Intel Raptor Lake CPUs has been further unpacked by the researchers who first disclosed it. DMPs are present on all Apple M-series CPUs and Intel's Raptor Lake processors, and the dedicated website for GoFetch now shows how exactly the exploit is carried out.

Customers of bankrupt crypto platform BlockFi have been targeted with a very convincing phishing email impersonating the platform, asking them to connect their wallet to complete the withdrawal of remaining funds. BlockFi was a digital asset lender that filed for Chapter 11 bankruptcy protection after it lost access to funds in the wake of the bankruptcy of the FTX cryptocurrency exchange and the Silicon Valley Bank shutdown.
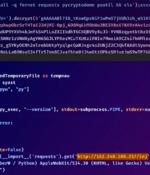
Unidentified adversaries orchestrated a sophisticated attack campaign that has impacted several individual developers as well as the GitHub organization account associated with Top.gg, a Discord...

In January 2024, Microsoft discovered they’d been the victim of a hack orchestrated by Russian-state hackers Midnight Blizzard (sometimes known as Nobelium). The concerning detail about this case...

Google's new AI-powered 'Search Generative Experience' algorithms recommend scam sites that redirect visitors to unwanted Chrome extensions, fake iPhone giveaways, browser spam subscriptions, and tech support scams. Earlier this month, Google began rolling out a new feature called Google Search Generative Experience in its search results, which provides AI-generated quick summaries for search queries, including recommendations for other sites to visit related to the query.