Security News > 2023 > August

A new version of the DreamBus botnet malware exploits a critical-severity remote code execution vulnerability in RocketMQ servers to infect devices. The recent DreamBus attacks leveraging that flaw were spotted by researchers at the Juniper Threat Labs, who reported a spike in the activity in mid-June 2023.

The Qakbot botnet has been crippled by the US Department of Justice: 52 of its servers have been seized and the popular malware loader has been removed from over 700,000 victim computers around the world. "To disrupt the botnet, the FBI was able to redirect Qakbot botnet traffic to and through servers controlled by the FBI, which in turn instructed infected computers in the United States and elsewhere to download a file created by law enforcement that would uninstall the Qakbot malware. This uninstaller was designed to untether the victim computer from the Qakbot botnet, preventing further installation of malware through Qakbot," the Department explained.

A novel Android banking malware named MMRat utilizes a rarely used communication method, protobuf data serialization, to more efficiently steal data from compromised devices. The performance would hinder threat actors from executing bank fraud effectively, which is why MMRat's authors have opted to develop a custom Protobuf protocol for data exfiltration.

At its Google Next '23 event this week, Google revealed how - with the use of its PaLM 2 foundational model - it is applying the generative AI Duet AI to security solutions in Google Cloud, including posture management, threat intelligence and detection and network and data security. Integrating Duet AI into Chronicle explicitly addresses security operations workload and tool proliferation, and implicitly the shortage of security operators in SOC teams, Potti explained.

Qakbot, one of the largest and longest-running botnets to date, was taken down following a multinational law enforcement operation spearheaded by the FBI and known as Operation 'Duck Hunt.' [...]

Because the investigation identified the presence of tools that could be used for data exfiltration, we can't rule out the possibility that data was taken from one of our file servers. PurFoods says it has contacted everyone whose was affected, or at least everyone whose data appeared in one or more of the scrambled files, which we assume are the files that the company thinks the attackers would have stolen, if indeed any data was exfiltrated.

Microsoft announced today that Exchange Server 2016 and 2019 now come with support for HTTP Strict Transport Security. Microsoft provides detailed information on configuring HSTS on Exchange Server 2016 and 2019 via PowerShell or the Internet Information Services Manager on its documentation website.

According to the report, attackers favor Microsoft because of the potential to move laterally through an organization's Microsoft environments. If 4.31% seems like a small figure, Abnormal Security CISO Mike Britton pointed out that it is still four times the impersonation volume of the second most-spoofed brand, PayPal, which was impersonated in 1.05% of the attacks Abnormal tracked.
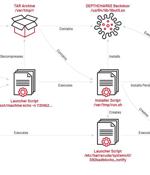
A suspected Chinese-nexus hacking group exploited a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway appliances to breach government, military, defense and aerospace, high-tech industry, and telecom sectors as part of a global espionage campaign. What's more, FOXTROT shares overlaps with an open-source rootkit called Reptile, which has been extensively used by multiple Chinese hacking crews in recent months.

Hackers are using a critical exploit chain to target Juniper EX switches and SRX firewalls via their Internet-exposed J-Web configuration interface. One week after Juniper disclosed and released security updates to patch the four flaws that can be chained to achieve remote code execution, watchTowr Labs security researchers released a proof-of-concept exploit targeting the SRX firewall bugs.