Security News > 2023 > July

The prolific China-linked nation-state actor known as APT41 has been linked to two previously undocumented strains of Android spyware called WyrmSpy and DragonEgg. "Known for its exploitation of web-facing applications and infiltration of traditional endpoint devices, an established threat actor like APT 41 including mobile in its arsenal of malware shows how mobile endpoints are high-value targets with coveted corporate and personal data," Lookout said in a report shared with The Hacker News.

The U.S. government has banned European commercial spyware manufacturers Intellexa and Cytrox, citing risks to U.S. national security and foreign policy interests. Google's Threat Analysis Group linked the Cytrox in May 2022 with multiple zero-day vulnerabilities used to deploy Predator spyware on Android devices.

In light of these events, I'd like to discuss how OSINT can assist with dark web investigations. Transactions on the dark web often involve cryptocurrency in exchange for illegal goods and services.

This live virtual event brings together industry leaders, experts, and professionals to explore the future of network security. With an alarming 96 percent of organizations falling victim to cyberattacks in 2021, INTERSECT '23 offers invaluable insights into leveraging cutting-edge network security platforms to fortify defenses against evasive zero-day threats.
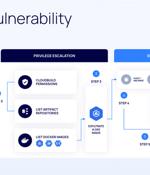
Cybersecurity researchers have uncovered a privilege escalation vulnerability in Google Cloud that could enable malicious actors tamper with application images and infect users, leading to supply chain attacks. The issue, dubbed Bad.Build, is rooted in the Google Cloud Build service, according to cloud security firm Orca, which discovered and reported the issue.

Citrix has patched three vulnerabilities in NetScaler ADC and NetScaler Gateway, one of which is a zero-day being exploited by attackers. In early 2022, the company reported the exploitation of a RCE vulnerability in its Citrix ADC deployments by a Chinese state-sponsored group.

FBI warns of a surge in tech support scams targeting the elderly across the United States and urging victims to dispatch cash concealed within magazines or similar items through shipping firms. While tech support scams have been around for years, the FBI says this is a departure from scammers' conventional tactics of soliciting their targets to send money using bank transfers, cryptocurrencies, or gift cards.

There's no reason to take chances of your business suffering a data breach when a lifetime of powerful protection is so affordable. It's one thing to be diligent about keeping your personal information protected while browsing online, but it's quite another to protect the sensitive data your business needs to keep it running.

The U.S. government on Tuesday added two foreign commercial spyware vendors, Cytrox and Intellexa, to an economic blocklist for weaponizing cyber exploits to gain unauthorized access to devices and "Threatening the privacy and security of individuals and organizations worldwide." Cytrox is the maker of a mobile mercenary spyware called Predator that's analogous to NSO Group's Pegasus.

Hive is widely believed to be affiliated with the Conti ransomware group, joining a list of other groups associated with former Conti operators, including Royal, Black Basta, and Quantum. Hive, like other RaaS providers, wrote a ransomware encryptor, created a dark web domain, advertised their services to affiliates and forums, and then allowed users to purchase a license to configure a ransomware payload and receive extortion funds.