Security News > 2022 > September

Germany's Bundeskriminalamt, the country's federal criminal police, carried out raids on the homes of three individuals yesterday suspected of orchestrating large-scale phishing campaigns that defrauded internet users of €4,000,000. The three men obtained money from their victims by sending them phishing emails that were clones of messages from real German banks.

Back in 2018, we learned that covert system of websites that the CIA used for communications was compromised by-at least-China and Iran, and that the blunder caused a bunch of arrests, imprisonments, and executions. We're now learning that the CIA is still "Using an irresponsibly secured system for asset communication."

Unknown attackers wielding novel specialized malware have managed to compromise VMware ESXi hypervisors and guest Linux and Windows virtual machines, Mandiant threat analysts have discovered. VirtualGATE is a utility program that incorporates a memory-only dropper and a payload that can run commands from a hypervisor host on a guest virtual machine, or between guest virtual machines on the same hypervisor host.

An espionage-focused threat actor has been observed using a steganographic trick to conceal a previously undocumented backdoor in a Windows logo in its attacks against Middle Eastern governments. Symantec's latest analysis of attacks between February and September 2022, during which the group targeted the governments of two Middle Eastern countries and the stock exchange of an African nation, highlights the use of a new backdoor called Stegmap.
A social engineering campaign leveraging job-themed lures is weaponizing a years-old remote code execution flaw in Microsoft Office to deploy Cobalt Strike beacons on compromised hosts. "The payload discovered is a leaked version of a Cobalt Strike beacon," Cisco Talos researchers Chetan Raghuprasad and Vanja Svajcer said in a new analysis published Wednesday.

Malware disabling/abusing EDR agents: The emergence of sophisticated hacker groups like Lapsus$ is another risk that EDR tools can't deal with. Maintaining/deploying EDR: Finally, with agent based EDR products, it can be a huge burden for security teams to install and maintain agents on every endpoint across the enterprise network environment.
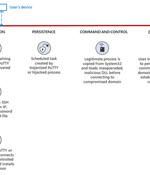
A "Highly operational, destructive, and sophisticated nation-state activity group" with ties to North Korea has been weaponizing open source software in their social engineering campaigns aimed at companies around the world since June 2022. Attacks targeted employees in organizations across multiple industries, including media, defense and aerospace, and IT services in the U.S., the U.K., India, and Russia.

Microsoft is now blocking the Windows 11 22H2 update from being offered because of compatibility issues affecting Windows devices with printers using Microsoft IPP Class Driver or Universal Print Class Driver. "Windows needs connectivity to the printer to identify all the features of the printer. Without connectivity, the printer is set up with default settings and in some scenarios might not get updated once connectivity to the printer is restored," Microsoft explained.

Attackers are leveraging two zero-day vulnerabilities to breach Microsoft Exchange servers."At this time, Microsoft is aware of limited targeted attacks using the two vulnerabilities to get into users' systems. In these attacks, CVE-2022-41040 can enable an authenticated attacker to remotely trigger CVE-2022-41082. It should be noted that authenticated access to the vulnerable Exchange Server is necessary to successfully exploit either of the two vulnerabilities."

Microsoft officially disclosed it investigating two zero-day security vulnerabilities impacting Exchange Server 2013, 2016, and 2019 following reports of in-the-wild exploitation. "The first vulnerability, identified as CVE-2022-41040, is a Server-Side Request Forgery vulnerability, while the second, identified as CVE-2022-41082, allows remote code execution when PowerShell is accessible to the attacker," the tech giant said.