Security News > 2022 > September

Microsoft has released the Windows 11 22H2 KB5017389 preview cumulative update with 30 fixes or improvements. This Windows 11 update is part of Microsoft's September 2022 monthly "C" update, allowing users to test upcoming fixes coming in the October 2022 Patch Tuesday.

Japanese scientists are trying to breed the oval squid in captivity. As usual, you can also use this squid post to talk about the security stories in the news that I haven't covered.

As expected, threat actors now use the leaked LockBit 3.0 ransomware builder for their ransomware operations. Another interesting research is the prediction that ransomware gangs may move away from encrypting altogether and switch to pure data exfiltration and file deletion to cut out the ransomware developer.

This cloud storage with NAS support costs less than you think We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. In a special deal for TechRepublic readers, you can currently get 1TB of storage for $38.99 on a two-year subscription.

15 highest-paying certifications for 2022 We may be compensated by vendors who appear on this page through methods such as affiliate links or sponsored partnerships. The focus on cybersecurity and cloud certifications confirms the trend seen in the 2021 report in which the same two areas commanded the top salaries.

Just having your Exchange server accessible to email users over the internet is not enough on its own to expose you to attack, because so-called unauthenticated invocation of these bugs is not possible. According to Microsoft, blocking TCP ports 5985 and 5986 on your Exchange server will limit attackers from chaining from the first vulnerability to the second.

The Cybersecurity and Infrastructure Security Agency has added three more security flaws to its list of bugs exploited in attacks, including a Bitbucket Server RCE and two Microsoft Exchange zero-days.While Microsoft hasn't yet released security updates to address this pair of actively exploited bugs, it shared mitigation measures requiring customers to add an IIS server blocking rule that would block attack attempts.

A new phishing campaign targets US and New Zealand job seekers with malicious documents installing Cobalt Strike beacons for remote access to victims' devices. The discovery comes from researchers at Cisco Talos who observed two different phishing lures, both targeting job seekers and leading to the deployment of Cobalt Strike.

The Australian Federal Police announced today the launch of Operation Guardian to ensure that more than 10,000 customers who had their info leaked in the Optus data breach will get priority protection against fraud attempts. Throughout Operation Guardian, JPC3 members can use full and collective legislative powers and investigative and intelligence capabilities of all Australian policing jurisdictions to help boost the breach victims' protection against fraudsters.
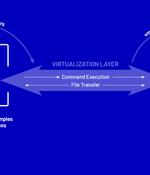
Threat actors have been found deploying never-before-seen post-compromise implants in VMware's virtualization software to seize control of infected systems and evade detection. Google's Mandiant threat intelligence division referred to it as a "Novel malware ecosystem" that impacts VMware ESXi, Linux vCenter servers, and Windows virtual machines, allowing attackers to maintain persistent access to the hypervisor as well as execute arbitrary commands.