Security News > 2021 > August

The names and home addresses of 111,000 British firearm owners have been dumped online as a Google Earth-compatible. Dumped online last week onto an animal rights activist's blog, the reformatted Guntrader breach data was explicitly advertised as being importable into Google Earth so randomers could "Contact as many [owners] as you can in your area and ask them if they are involved in shooting animals."

For companies going fully remote again, team cohesion, cloud investments and reducing IT burden could be key, according to tech experts. After a year of remote work, companies were starting to bring employees back to the office, but the more contagious delta variant and surging COVID-19 cases are giving employers pause; complicating office reentry timelines.

Whether the app is on your mobile device, entertainment system or garage door, APIs are what developers use to make applications function. Some background on what makes APIs such a security concern.

Microsoft has announced that Windows 11 will be released on October 5th, 2021, to Windows 10 users with support devices. Windows 11 is the first major version of Windows released since 2015, when Windows 10 was released.

Companies should now consider cybercriminals as business competitors, according to Lacework's 2021 Cloud Threat Report Volume 2. The Lacework Lab analyzed telemetry from its customers and other data to identify rising and increasing security threats to cloud deployments.

Late last year, the NSA declassified and released a redacted version of Lambros D. Callimahos’s Military Cryptanalytics, Part III. We just got most of the index. It’s hard to believe that there...

"Many schools cannot operate without their computer systems, and some schools have had to cancel classes due to ransomware attacks," said Paul Bischoff, privacy advocate at Comparitech. "Resolving a ransomware attack without paying the ransom takes about two weeks on average, which is far too long for kids to be out of school. So ransomware creates urgency that makes schools more likely to pay up."

The threat, dubbed LockFile, uses a unique "Intermittent encryption" method as a way to evade detection as well as adopting tactics from previous ransomware gangs. Discovered by researchers at Sophos, LockFile ransomware encrypts every 16 bytes of a file, which means some ransomware protection solutions don't notice it because "An encrypted document looks statistically very similar to the unencrypted original," Mark Loman, director, engineering, for next-gen technologies at Sophos, wrote in a report on LockFile published last week.

Tapping into leading edge cyber security knowledge can be like listening to the radio. We think you'll be pleased to know that Sophos' Security SOS Week returns to a screen and headset near you from September 13 to 16.
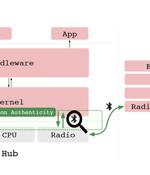
A group of academics has proposed a machine learning approach that uses authentic interactions between devices in Bluetooth networks as a foundation to handle device-to-device authentication reliably. Called "Verification of Interaction Authenticity", the recurring authentication scheme aims to solve the problem of passive, continuous authentication and automatic deauthentication once two devices are paired with one another, which remain authenticated until an explicit deauthentication action is taken, or the authenticated session expires.