Security News

A previously undocumented backdoor named Msupedge has been put to use against a cyber attack targeting an unnamed university in Taiwan. "The most notable feature of this backdoor is that it communicates with a command-and-control server via DNS traffic," the Symantec Threat Hunter Team, part of Broadcom, said in a report shared with The Hacker News.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical security flaw impacting Jenkins to its Known Exploited Vulnerabilities (KEV) catalog, following its...

As Microsoft explained in its Tuesday advisory, unauthenticated attackers can exploit the flaw remotely in low-complexity attacks by repeatedly sending IPv6 packets that include specially crafted packets. Microsoft also shared its exploitability assessment for this critical vulnerability, tagging it with an "Exploitation more likely" label, which means that threat actors could create exploit code to "Consistently exploit the flaw in attacks."
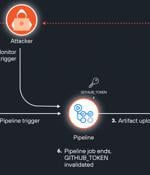
A newly discovered attack vector in GitHub Actions artifacts dubbed ArtiPACKED could be exploited to take over repositories and gain access to organizations' cloud environments."A combination of misconfigurations and security flaws can make artifacts leak tokens, both of third party cloud services and GitHub tokens, making them available for anyone with read access to the repository to consume," Palo Alto Networks Unit 42 researcher Yaron Avital said in a report published this week.

The maintainers of the FreeBSD Project have released security updates to address a high-severity flaw in OpenSSH that attackers could potentially exploit to execute arbitrary code remotely with elevated privileges. The vulnerability, tracked as CVE-2024-7589, carries a CVSS score of 7.4 out of a maximum of 10.0, indicating high severity.

Microsoft has disclosed an unpatched zero-day in Office that, if successfully exploited, could result in unauthorized disclosure of sensitive information to malicious actors. The vulnerability, tracked as CVE-2024-38200, has been described as a spoofing flaw that affects the following versions of Office -.

A "0.0.0.0-Day" vulnerability affecting Chrome, Safari and Firefox can be - and has been - exploited by attackers to gain access to services on internal networks, Oligo Security researchers have revealed. The vulnerability stems from how those popular browsers handle network requests from external, public websites, and may allow attackers to change settings, gain access to protected information, uploading malicious models, or even achieve remote code execution.

Cybersecurity researchers have discovered a new "0.0.0.0 Day" impacting all major web browsers that malicious websites could take advantage of to breach local networks. The critical vulnerability "Exposes a fundamental flaw in how browsers handle network requests, potentially granting malicious actors access to sensitive services running on local devices," Oligo Security researcher Avi Lumelsky said.

Google has addressed a high-severity security flaw impacting the Android kernel that it has been actively exploited in the wild. That said, Clement Lecigne of Google's Threat Analysis Group has been credited with reporting the flaw, suggesting that it's likely being exploited by commercial spyware vendors to infiltrate Android devices in narrowly targeted attacks.

Thousands of accounts have been exposed after hackers used existing emails to create Google Workspace accounts and bypassed the verification process. One impacted user that shared their experience on a Google Cloud Community forum was notified by Google that someone had created a Workspace account with their email without verification and then used it to log into Dropbox.