Security News

A Telegram for Android zero-day vulnerability dubbed 'EvilVideo' allowed attackers to send malicious Android APK payloads disguised as video files. A threat actor named 'Ancryno' first began selling the Telegram zero-day exploit on June 6, 2024, in a post on the Russian-speaking XSS hacking forum, stating the flaw existed in Telegram v10.14.4 and older.

A new trove of 361 million email addresses has been added to Have I Been Pwned?, the free online service through which users can check whether their account credentials and other data has been compromised in one or more data breaches. The data includes lists of credentials for accounts grouped either by service or country.

A massive trove of 361 million email addresses from credentials stolen by password-stealing malware, in credential stuffing attacks, and from data breaches was added to the Have I Been Pwned data breach notification service, allowing anyone to check if their accounts have been compromised. Cybersecurity researchers collected these credentials from numerous Telegram cybercrime channels, where the stolen data is commonly leaked to the channel's users to build reputation and subscribers.

Advertising presented to you on this service can be based on limited data, such as the website or app you are using, your non-precise location, your device type or which content you are interacting with. Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Telegram users are currently experiencing issues worldwide, with users unable to use the website and mobile apps. [...]

Telegram fixed a zero-day vulnerability in its Windows desktop application that could be used to bypass security warnings and automatically launch Python scripts. The next day, a proof of concept exploit was shared on the XSS hacking forum explaining that a typo in the source code for Telegram for Windows could be exploited to send Python.

This caused the file to automatically be executed by Python without a warning from Telegram like it does for other executables, and was supposed to do for this file if it wasn't for a typo. In a statement to BleepingComputer, Telegram rightfully disputes that the bug was a zero-click flaw but confirmed they fixed the "Issue" in Telegram for Windows to prevent Python scripts from automatically launching when clicked.
In June 2017, a study of more than 3,000 Massachusetts Institute of Technology (MIT) students published by the National Bureau for Economic Research (NBER) found that 98% of them were willing to...
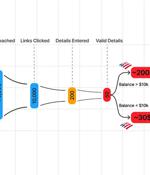
Cybersecurity researchers are calling attention to the "democratization" of the phishing ecosystem owing to the emergence of Telegram as an epicenter for cybercrime, enabling threat actors to...