Security News

Microsoft has detailed a new campaign in which attackers unsuccessfully attempted to move laterally to a cloud environment through a SQL Server instance. "The attackers initially exploited a SQL...

A cyberattack campaign is targeting exposed Microsoft SQL databases, aiming to deliver ransomware and Cobalt Strike payloads. The attackers target exposed MS SQL servers by brute-forcing access credentials.
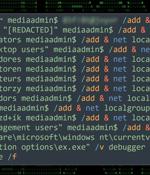
Threat actors are exploiting poorly secured Microsoft SQL servers to deliver Cobalt Strike and a ransomware strain called FreeWorld. "The ransomware payload of choice appears to be a newer variant of Mimic ransomware called FreeWorld."
Mallox ransomware activities in 2023 have witnessed a 174% increase when compared to the previous year, new findings from Palo Alto Networks Unit 42 reveal. "Mallox ransomware, like many other ransomware threat actors, follows the double extortion trend: stealing data before encrypting an organization's files, and then threatening to publish the stolen data on a leak site as leverage to convince victims to pay the ransom fee," security researchers Lior Rochberger and Shimi Cohen said in a new report shared with The Hacker News.
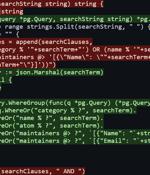
Multiple SQL injection vulnerabilities have been disclosed in Gentoo Soko that could lead to remote code execution on vulnerable systems. "These SQL injections happened despite the use of an Object-Relational Mapping library and prepared statements," SonarSource researcher Thomas Chauchefoin said, adding they could result in RCE on Soko because of a "Misconfiguration of the database."

Progress Software, the company behind the MOVEit Transfer application, has released patches to address brand new SQL injection vulnerabilities affecting the file transfer solution that could enable the theft of sensitive information. "Multiple SQL injection vulnerabilities have been identified in the MOVEit Transfer web application that could allow an unauthenticated attacker to gain unauthorized access to the MOVEit Transfer database," the company said in an advisory released on June 9, 2023.

A new security flaw has been disclosed in the Google Cloud Platform's Cloud SQL service that could be potentially exploited to obtain access to confidential data. "The vulnerability could have enabled a malicious actor to escalate from a basic Cloud SQL user to a full-fledged sysadmin on a container, gaining access to internal GCP data like secrets, sensitive files, passwords, in addition to customer data," Israeli cloud security firm Dig said.
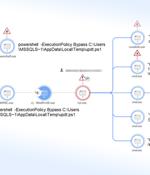
Poorly managed Microsoft SQL servers are the target of a new campaign that's designed to propagate a category of malware called CLR SqlShell that ultimately facilitates the deployment of cryptocurrency miners and ransomware. "Similar to web shell, which can be installed on web servers, SqlShell is a malware strain that supports various features after being installed on an MS SQL server, such as executing commands from threat actors and carrying out all sorts of malicious behavior," AhnLab Security Emergency response Center said in a report published last week.

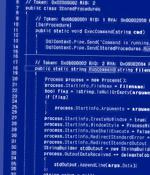
Attackers are hacking into poorly secured and Interned-exposed Microsoft SQL servers to deploy Trigona ransomware payloads and encrypt all files. Exe service, which they use to launch the Trigona ransomware as svchost.

A group of academics has demonstrated novel attacks that leverage Text-to-SQL models to produce malicious code that could enable adversaries to glean sensitive information and stage denial-of-service attacks. The findings, which were validated against two commercial solutions BAIDU-UNIT and AI2sql, mark the first empirical instance where natural language processing models have been exploited as an attack vector in the wild.