Security News

Cybersecurity researchers have flagged a new malicious campaign related to the North Korean state-sponsored threat actor known as Kimsuky that exploits a now-patched vulnerability impacting...

South Korea has formally suspended new downloads of Chinese artificial intelligence (AI) chatbot DeepSeek in the country until the service makes changes to its mobile apps to comply with data...
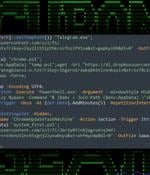
A nation-state threat actor with ties to North Korea has been linked to an ongoing campaign targeting South Korean business, government, and cryptocurrency sectors. The attack campaign, dubbed...

Evgenii Ptitsyn, a Russian national and suspected administrator of the Phobos ransomware operation, was extradited from South Korea and is facing cybercrime charges in the United States. [...]

Meta has been fined 21.62 billion won ($15.67 million) by South Korea's data privacy watchdog for illegally collecting sensitive personal information from Facebook users, including data about...

Unclear if this is a sign controversial service is cleaning up its act everywhere Controversial social network Telegram has co-operated with South Korean authorities and taken down 25 videos...

South Korea's ruling party, People Power Party (PPP), has issued an announcement stating that North Korean hackers have stolen crucial information about K2 tanks, the country's main battle tank,...

The North Korean hacker group Kimsuki has been using a new Linux malware called Gomir that is a version of the GoBear backdoor delivered via trojanized software installers. In early February 2024, researchers at the SW2 threat intelligence company reported about a campaign where Kimsuky used trojanized versions of various software solutions, e.g. TrustPKI and NX PRNMAN from SGA Solutions, Wizvera VeraPort, to infect South Korean targets with Troll Stealer and the Go-based Windows malware GoBear.

The North Korea-linked nation-state actor known as Kimsuky is suspected of using a previously undocumented Golang-based information stealer called Troll Stealer. The malware steals "SSH,...

Interpol on Tuesday revealed the results of what it's dubbed Operation HAECHI IV - a six-month effort that saw 34 nations cooperate, with funding from South Korea. The majority - about three quarters - of the crime investigated by the op was business email compromise, e-commerce fraud, and investment fraud.