Security News

Cybersecurity researchers have uncovered firmware security vulnerabilities in the Illumina iSeq 100 DNA sequencing instrument that, if successfully exploited, could permit attackers to brick or...
A high-severity security flaw has been disclosed in ProjectDiscovery's Nuclei, a widely-used open-source vulnerability scanner that, if successfully exploited, could allow attackers to bypass...

Cybersecurity researchers have flagged two malicious packages that were uploaded to the Python Package Index (PyPI) repository and came fitted with capabilities to exfiltrate sensitive information...

Malware that’s made specifically to target industrial control systems (ICS), Internet of Things (IoT) and operational technology (OT) control devices is still rare, but in the last few weeks...

A threat actor tracked as MUT-1244 by DataDog researchers has been targeting academics, pentesters, red teamers, security researchers, as well as other threat actors, in order to steal AWS access...

Details have emerged about a now-patched security vulnerability in Apple's iOS and macOS that, if successfully exploited, could sidestep the Transparency, Consent, and Control (TCC) framework and...

A previously undocumented Android spyware called 'EagleMsgSpy' has been discovered and is believed to be used by law enforcement agencies in China to monitor mobile devices. [...]

A suspected China-based threat actor has been linked to a series of cyber attacks targeting high-profile organizations in Southeast Asia since at least October 2023. The espionage campaign...

Details have emerged about a now-patched security flaw in the DeepSeek artificial intelligence (AI) chatbot that, if successfully exploited, could permit a bad actor to take control of a victim's...
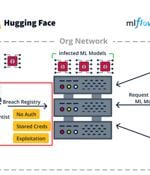
Cybersecurity researchers have disclosed multiple security flaws impacting open-source machine learning (ML) tools and frameworks such as MLflow, H2O, PyTorch, and MLeap that could pave the way...