Security News
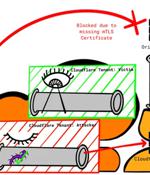
Firewall and distributed denial-of-service (DDoS) attack prevention mechanisms in Cloudflare can be circumvented by exploiting gaps in cross-tenant security controls, defeating the very purpose of...

Security researchers have spotted what they believe to be a "Possible mass exploitation" of vulnerabilities in Progress Software's WS FTP Server. Researchers at Rapid7 began noticing evidence of exploitation on 30 September across multiple instances of WS FTP. Progress released fixes for eight separate vulnerabilities in WS FTP on Wednesday, including one rated a maximum score of 10 on the CVSS severity scale.

Security researcher Sam Curry describes a stressful situation he encountered upon his return to the U.S. when border officials and federal agents seized and searched his electronic devices. Why, you ask? All because his IP address landed in the logs of a crypto wallet associated with a phishing scam that Curry had earlier helped investigate as a part of his job-a scam that the feds were now investigating.
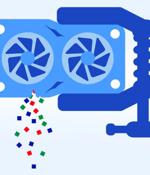
A novel side-channel attack called GPU.zip renders virtually all modern graphics processing units (GPU) vulnerable to information leakage. "This channel exploits an optimization that is data...

The peer-to-peer (P2) worm known as P2PInfect has witnessed a surge in activity since late August 2023, witnessing a 600x jump between September 12 and 19, 2023. "This increase in P2PInfect...
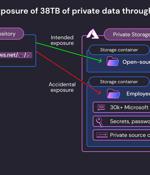
Microsoft on Monday said it took steps to correct a glaring security gaffe that led to the exposure of 38 terabytes of private data. "The exposure came as the result of an overly permissive SAS token - an Azure feature that allows users to share data in a manner that is both hard to track and hard to revoke," Wiz said in a report.

More details have emerged about a set of now-patched cross-site scripting flaws in the Microsoft Azure HDInsight open-source analytics service that could be weaponized by a threat actor to carry out malicious activities. "The identified vulnerabilities consisted of six stored XSS and two reflected XSS vulnerabilities, each of which could be exploited to perform unauthorized actions, varying from data access to session hijacking and delivering malicious payloads," Orca security researcher Lidor Ben Shitrit said in a report shared with The Hacker News.

North Korean threat actors are once again attempting to compromise security researchers' machines by employing a zero-day exploit. The warning comes from Google's own security researchers Clement Lecigne and Maddie Stone, who detailed the latest campaign mounted by government-backed attackers.

Threat actors associated with North Korea are continuing to target the cybersecurity community using a zero-day bug in unspecified software over the past several weeks to infiltrate their machines. A search on X shows that the now-suspended account has been active since at least October 2022, with the actor releasing proof-of-concept exploit code for high-severity privilege escalation flaws in the Windows Kernel such as CVE-2021-34514 and CVE-2022-21881.

Google's Threat Analysis Group says North Korean state hackers are again targeting security researchers in attacks using at least one zero-day in an undisclosed popular software. Researchers attacked in this campaign are involved in vulnerability research and development, according to Google's team of security experts that protects the company's users from state-sponsored attacks.