Security News

Encrypted messaging app Signal has pushed back against "viral reports" of an alleged zero-day flaw in its software, stating it found no evidence to support the claim. "After responsible...

Certain online risks to children are on the rise, according to a recent report from Thorn, a technology nonprofit whose mission is to build technology to defend children from sexual abuse....

How To Use This Report Enhance situational awareness of techniques used by threat actors Identify potential attacks targeting your industry Gain insights to help improve and accelerate your...
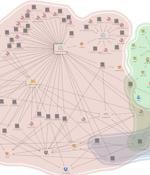
An unnamed Southeast Asian government has been targeted by multiple China-nexus threat actors as part of espionage campaigns targeting the region over extended periods of time. "While this...

Rogers customers, primarily those located in Downtown Toronto and parts of Ontario, are reporting outages this week affecting their internet service. Rogers customers took to X to voice their concerns about internet outages in their area.

This relatively low percentage reflects the current state of the industry, where vCISO services are still an emerging market. The vCISO landscape is expected to change dramatically by the end of 2024.

Total number of malware-based attacks: 1,578,733 Number of unique attacks: 200,454 Average number of cyberattacks per day: 17,280 Average number of cyberattacks per hour: 720 Average number of attacks per minute: 12 Average number of new malware variants per minute: 1.5. Attacks ramped up again as cybercriminals got back to work in the new year.

A new study by Critical Insight shows that cybersecurity attacks in the health care sector are hitting more individuals and finding vulnerabilities in third-party partners. A new study by cybersecurity firm Critical Insight noted that while the sheer number of breaches against health care facilities is actually down, there is a spike in the number of people who have been affected by attacks as well as an increase in supply chain and third-party targets.

A new State of SaaS Security Posture Management Report from SaaS cybersecurity provider AppOmni indicates that Cybersecurity, IT, and business leaders alike recognize SaaS cybersecurity as an increasingly important part of the cyber threat landscape. When asked to rate the SaaS cybersecurity maturity level of their organizations, 71% noted that their organizations' SaaS cybersecurity maturity has achieved either a mid-high level or the highest level.

Phishing is so last year: Akamai's report finds that zero-day and one-day vulnerabilities caused a 143% increase in total ransomware victims. Akamai's ransomware report released at Black Hat 2023 revealed that exploitation of zero-day and one-day vulnerabilities has led to a 143% increase in total ransomware victims with data exfiltration of files at the end of the kill chain, now the primary source of extortion.