Security News

Spring released emergency updates to fix the 'Spring4Shell' zero-day remote code execution vulnerability, which leaked prematurely online before a patch was released. Yesterday, an exploit for a zero-day remote code execution vulnerability in the Spring Framework dubbed 'Spring4Shell' was briefly published on GitHub and then removed.

Another Java Remote Code Execution vulnerability has reared its head, this time in the popular Spring Framework and, goodness, it's a nasty one. This is a severe remote code execution zero day that can be accessed over HTTP or HTTPS. "Spring have acknowledged the vulnerability and released 5.3.18 and 5.2.20 to patch the issue," said Sonatype, "We recommend an immediate upgrade for all users."

A zero-day remote code execution vulnerability has come to light in the Spring framework shortly after a Chinese security researcher briefly leaked a proof-of-concept exploit on GitHub before deleting their account. According to cybersecurity firm Praetorian, the unpatched flaw impacts Spring Core on Java Development Kit versions 9 and later and is a bypass for another vulnerability tracked as CVE-2010-1622, enabling an unauthenticated attacker to execute arbitrary code on the target system.

A critical security vulnerability has bloomed in the Spring Cloud Function, which could lead to remote code execution and the compromise of an entire internet-connected host. Spring Cloud is an open-source microservices framework: A collection of ready-to-use components which are useful in building distributed applications in an enterprise.

A critical vulnerability in Sophos Firewall in being exploited in the wild to target "a small set of specific organizations primarily in the South Asia region," Sophos has warned. CVE-2022-1040 is an authentication bypass vulnerability in the User Portal and Webadmin of Sophos Firewall, and can be exploited by attackers to achieve remote code execution on vulnerable appliances.

Cybersecurity firm Sophos on Monday warned that a recently patched critical security vulnerability in its firewall product is being actively exploited in real-world attacks.The flaw, tracked as CVE-2022-1040, is rated 9.8 out of 10 on the CVSS scoring system and impacts Sophos Firewall versions 18.5 MR3 and older.

Cybersecurity stalwart Sophos has plugged a critical vulnerability in its firewall product, which could allow remote code-execution. The flaw, tracked as CVE-2022-1040, is specifically an authentication-bypass vulnerability in the User Portal and Webadmin of the Sophos Firewall.
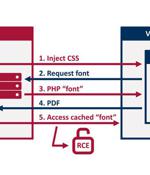
Researchers have disclosed an unpatched security vulnerability in "Dompdf," a PHP-based HTML to PDF converter, that, if successfully exploited, could lead to remote code execution in certain configurations. In other words, the flaw allows a malicious party to upload font files with a.php extension to the web server, which can then be activated by using an XSS vulnerability to inject HTML into a web page before it's rendered as a PDF. This meant that the attacker could potentially navigate to the uploaded.

Veeam Software has patched two critical vulnerabilities affecting its popular Veeam Backup & Replication solution, which could be exploited by unauthenticated attackers to remotely execute malicious code.Veeam Backup & Replication is an enteprise data protection solution that allows admins to create image-level backups of virtual, physical, cloud machines and restore from them.

Researchers have disclosed three security vulnerabilities affecting Pascom Cloud Phone System that could be combined to achieve a full pre-authenticated remote code execution of affected systems. Kerbit security researcher Daniel Eshetu said the shortcomings, when chained together, can lead to "An unauthenticated attacker gaining root on these devices."