Security News
The vulnerability in question is CVE-2024-4577, which allows an attacker to remotely execute malicious commands on Windows systems using Chinese and Japanese language locales. The disclosure comes as Cloudflare said it recorded a 20% year-over-year increase in DDoS attacks in the second quarter of 2024, and that it mitigated 8.5 million DDoS attacks during the first six months.

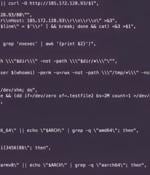
An OS command injection vulnerability in Windows-based PHP in CGI mode is being exploited by the TellYouThePass ransomware gang. Imperva says the attacks started on June 8, two days after the PHP development team pushed out fixes, and one day after Watchtowr researchers published a technical analysis of the flaw and proof-of-concept exploit code.

The TellYouThePass ransomware gang has been exploiting the recently patched CVE-2024-4577 remote code execution vulnerability in PHP to deliver webshells and execute the encryptor payload on target systems. TellYouThePass ransomware is known for quickly jumping on public exploits for vulnerabilities with a wide impact.

Details have emerged about a new critical security flaw impacting PHP that could be exploited to achieve remote code execution under certain circumstances. The vulnerability, tracked as...

A new PHP for Windows remote code execution vulnerability has been disclosed, impacting all releases since version 5.x, potentially impacting a massive number of servers worldwide. The new RCE flaw tracked as CVE-2024-4577, was discovered by Devcore Principal Security Researcher Orange Tsai on May 7, 2024, who reported it to the PHP developers.

The premium WordPress plugin 'Gravity Forms,' currently used by over 930,000 websites, is vulnerable to unauthenticated PHP Object Injection. Gravity Forms is a custom form builder website owners use for creating payment, registration, file upload, or any other form required for visitor-site interactions or transactions.

Like PyPI for Pythonistas, Gems for Ruby fans, NPM for JavaScript programmers, or LuaRocks for Luaphiles, Packagist is a repository where community contributors can publish details of PHP packages they've created. Unlike PyPI, which provides its own servers where the actual library code is stored, Packagist links to, but doesn't itself keep copies of, the code you need to download. There's an upside to doing it this way, notably that projects that are managed via well-known source code services such as GitHub don't need to maintain two copies of their official releases, which helps avoid the problem of "Version drift" between the source code control system and the packaging system.

PHP software package repository Packagist revealed that an "Attacker" gained access to four inactive accounts on the platform to hijack over a dozen packages with over 500 million installs to date. "The attacker forked each of the packages and replaced the package description in composer.json with their own message but did not otherwise make any malicious changes," Packagist's Nils Adermann said.

The researcher reached out to BleepingComputer stating that by hijacking these packages he hopes to get a job. Yesterday, a researcher with the pseudonym 'neskafe3v1' reached out to BleepingComputer stating he had taken over fourteen Packagist packages, with one of them having over 500 million installs.

This official implementation, known as XKCP, short for eXtended Keccak Code Package, is a collection of open source library code for Keccak and a range of related cryptographic tools from the Keccak team, including their authenticated encryption algorithms Ketje and Keyak, pseudorandom generators called Kravatte and Xoofff, and a lightweight encryption algorithm for low-power processors called Xoodyak. As you can imagine, code that hashes remotely uploaded data is likely either to retrieve the entire object before hashing it locally, typically by processing a fixed-length buffer of much smaller size over and over, or to fold each received chunk into the hash as it goes, typically receiving far more modestly-sized chunks at each network call.