Security News

The firm used its own AI models to determine that certain emails sent to its customers later identified as phishing attacks were probably AI-generated, according to Dan Shiebler, head of machine learning at Abnormal. "The danger of generative AI in email attacks is that it allows threat actors to write increasingly sophisticated content, making it more likely that their target will be deceived into clicking a link or following their instructions," he said, adding that AI can also be used to create greater personalization.

Attacks on commerce are booming, according to a new study by security firm Akamai. Bots raining on retail drive flood in commerce attacks.

A report from the Microsoft Defender Experts reveals a new multi-staged adversary in the middle phishing attack combined with a business email compromise attack targeting banking and financial institutions. The phishing email impersonates one of the target's trusted vendors to appear more legitimate and blend with legitimate email traffic and bypass detections, especially when an organization has policies to automatically allow emails from trusted vendors.

A widespread brand impersonation campaign targeting over a hundred popular apparel, footwear, and clothing brands has been underway since June 2022, tricking people into entering their account credentials and financial information on fake websites. The researchers say that the campaign operated over ten fake websites for Nike, Puma, and Clarks, featuring a design very similar to the official sites of the brands.
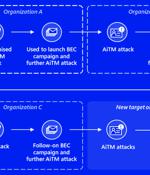
Banking and financial services organizations are the targets of a new multi-stage adversary-in-the-middle phishing and business email compromise attack, Microsoft has revealed. "The attack originated from a compromised trusted vendor and transitioned into a series of AiTM attacks and follow-on BEC activity spanning multiple organizations," the tech giant disclosed in a Thursday report.

A Chinese-speaking phishing gang dubbed PostalFurious has been linked to a new SMS campaign that's targeting users in the U.A.E. by masquerading as postal services and toll operators, per Group-IB. The fraudulent scheme entails sending users bogus text messages asking them to pay a vehicle trip fee to avoid additional fines. The messages also contain a shortened URL to conceal the actual phishing link.

A 25% increase in the use of phishing kits has been recorded in 2022, according to Group-IB. The key phishing trends observed are the increasing use of access control and advanced detection evasion techniques. The rise in evasive tactics, such as antibot techniques and randomization, poses a significant challenge for conventional detection systems and extends the lifespan of phishing campaigns.

A new 'File Archivers in the Browser' phishing kit abuses ZIP domains by displaying fake WinRAR or Windows File Explorer windows in the browser to convince users to launch malicious files. D0x has developed a clever phishing toolkit that lets you create fake in-browser WinRar instances and File Explorer Windows that are displayed on ZIP domains to trick users into thinking they are opened.

Wireless Broadband Alliance CEO on key drivers for Wi-Fi adoption in enterprise networksThis Help Net Security interview with Tiago Rodrigues, CEO at Wireless Broadband Alliance, delves into the future of enterprise networking, exploring the significant role of Wi-Fi 6E and Private 5G. Navigating the quantum leap in cybersecurityIn this Help Net Security interview, we sit down with Dr. Atsushi Yamada, the newly appointed CEO of ISARA, a security solutions company specializing in creating quantum-safe cryptography. Barracuda email security appliances hacked via zero-day vulnerabilityA vulnerability in Barracuda Networks' Email Security Gateway appliances has been exploited by attackers, the company has warned.

Perception Point's team has identified a 356% increase in the number of advanced phishing attacks attempted by threat actors in 2022. Overall, the total number of attacks increased by 87%, highlighting the growing threat that cyber attacks now pose to organizations.