Security News

Government entities in the Middle East have been targeted as part of a previously undocumented campaign to deliver a new backdoor dubbed CR4T. Russian cybersecurity company Kaspersky said it...

Cybercriminals are selling custom Raspberry Pi software called 'GEOBOX' on Telegram, which allows inexperienced hackers to convert the mini-computers into anonymous cyberattack tools. GEOBOX is sold on Telegram channels for a subscription of $80 per month or $700 for a lifetime license, payable in cryptocurrency.

A previously unknown malware campaign called Sign1 has infected over 39,000 websites over the past six months, causing visitors to see unwanted redirects and popup ads. The threat actors inject the malware into custom HTML widgets and legitimate plugins on WordPress sites to inject the malicious Sign1 scripts rather than modifying the actual WordPress files.

A stealthy advanced persistent threat tracked as Gelsemium was observed in attacks targeting a Southeast Asian government that spanned six months between 2022 and 2023. Gelsemium is a cyberespionage group operational since 2014, targeting government, education, and electronic manufacturers in East Asia and the Middle East.

Security researchers are warning of increased phishing activity that abuses Google Accelerated Mobile Pages to bypass email security measures and get to inboxes of enterprise employees. Google AMP is an open-source HTML framework co-developed by Google and 30 partners to make web content load faster on mobile devices.

In yet another sign of a lucrative crimeware-as-a-service ecosystem, cybersecurity researchers have discovered a new Windows-based information stealer called Meduza Stealer that's actively being developed by its author to evade detection by software solutions. "The Meduza Stealer has a singular objective: comprehensive data theft," Uptycs said in a new report.

An analysis of the "Evasive and tenacious" malware known as QBot has revealed that 25% of its command-and-control servers are merely active for a single day. What's more, 50% of the servers don't remain active for more than a week, indicating the use of an adaptable and dynamic C2 infrastructure, Lumen Black Lotus Labs said in a report shared with The Hacker News.

A 25% increase in the use of phishing kits has been recorded in 2022, according to Group-IB. The key phishing trends observed are the increasing use of access control and advanced detection evasion techniques. The rise in evasive tactics, such as antibot techniques and randomization, poses a significant challenge for conventional detection systems and extends the lifespan of phishing campaigns.
Cybersecurity researchers have detailed the inner workings of a highly evasive loader named "In2al5d p3in4er" that's used to deliver the Aurora information stealer malware. "The in2al5d p3in4er loader is compiled with Embarcadero RAD Studio and targets endpoint workstations using advanced anti-VM technique," cybersecurity firm Morphisec said in a report shared with The Hacker News.
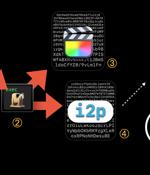
Trojanized versions of legitimate applications are being used to deploy evasive cryptocurrency mining malware on macOS systems. "This malware makes use of the Invisible Internet Project to download malicious components and send mined currency to the attacker's wallet," Jamf researchers Matt Benyo, Ferdous Saljooki, and Jaron Bradley said in a report shared with The Hacker News.