Security News

File hosting service Dropbox has confirmed that attackers have breached the Dropbox Sign production environment and accessed customer personal and authentication information. "Based on our investigation, a third party gained access to a Dropbox Sign automated system configuration tool. The actor compromised a service account that was part of Sign's back-end, which is a type of non-human account used to execute applications and run automated services. As such, this account had privileges to take a variety of actions within Sign's production environment."

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has added a critical flaw impacting GitLab to its Known Exploited Vulnerabilities (KEV) catalog, owing to active exploitation in...

The exploitation of vulnerabilities as an initial point of entry almost tripled from the previous year, accounting for 14% of all breaches, according to Verizon's 2024 Data Breach Investigations Report, which analyzed a record-high 30,458 security incidents and 10,626 confirmed breaches in 2023. "This year's DBIR findings reflect the evolving landscape that today's CISO's must navigate - balancing the need to address vulnerabilities quicker than ever before while investing in the continued employee education as it relates to ransomware and cybersecurity hygiene," said Craig Robinson, Research VP, Security Services at IDC. "The breadth and depth of the incidents examined in this report provides a window into how breaches are occurring, and despite the low-level of complexity are still proving to be incredibly costly for enterprises."

This highlights how digitally connected organizations are dependent on each other, and when one link in the supply chain is broken it can have a cascading effect on others. As soon as an organization's data moves over to a third party, the risks around it increase.
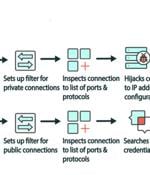
A new malware called Cuttlefish is targeting small office and home office (SOHO) routers with the goal of stealthily monitoring all traffic through the devices and gather authentication data from...

Learn how these regulations interact, their implications for both public and private sectors, and their role in shaping future AI and data privacy practices globally. Amid a recent uptick in laws and regulations being developed within the European Union, three EU-based data regulations are especially important to pay attention to, as they will influence data practices across a range of critical sectors.

ReNgine is an open-source automated reconnaissance framework for web applications that focuses on a highly configurable and streamlined recon process. ReNgine was developed to overcome the constraints of conventional reconnaissance tools.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.