Security News
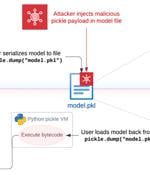
The security risks posed by the Pickle format have once again come to the fore with the discovery of a new "hybrid machine learning (ML) model exploitation technique" dubbed Sleepy Pickle. The...

The threat actor known as Arid Viper has been attributed to a mobile espionage campaign that leverages trojanized Android apps to deliver a spyware strain dubbed AridSpy. "The malware is...

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

An OS command injection vulnerability in Windows-based PHP in CGI mode is being exploited by the TellYouThePass ransomware gang. Imperva says the attacks started on June 8, two days after the PHP development team pushed out fixes, and one day after Watchtowr researchers published a technical analysis of the flaw and proof-of-concept exploit code.

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Recent supply chain cyber-attacks are prompting cyber security regulations in the financial sector to tighten compliance requirements, and other industries are expected to follow. Many companies...

Deepfakes were not the only manifestation of AI in the Indian elections. Long before the election began, Indian Prime Minister Narendra Modi addressed a tightly packed crowd celebrating links between the state of Tamil Nadu in the south of India and the city of Varanasi in the northern state of Uttar Pradesh.

Threat actors with ties to Pakistan have been linked to a long-running malware campaign dubbed Operation Celestial Force since at least 2018. The activity, still ongoing, entails the use of an...

The nascent malware known as SSLoad is being delivered by means of a previously undocumented loader called PhantomLoader, according to findings from cybersecurity firm Intezer. "The loader is...

If we abandon the ethics of cyber war, we might as well stop defending liberal democracies, because we're behaving like our opponents want us to behave. Traditionally, western countries did not invest in non-kinetic cyber warfare because at the time the West held the upper hand in terms of superior technologies that allowed it more room to maneuver in this domain.