Security News

Russian APT28 military hackers used Microsoft Outlook zero-day exploits to target multiple European NATO member countries, including a NATO Rapid Deployable Corps. The Russian hackers are also tracked as Fighting Ursa, Fancy Bear, and Sofacy, and they've been previously linked to Russia's Main Intelligence Directorate, the country's military intelligence service.

A Belgian man has been arrested and charged for his role in a years-long smuggling scheme to export military-grade electronics from the US to Russia and China. Belgian law enforcement detained Hans Maria De Geetere, 61, and five others for questioning on December 5.

Professors at the University of South Australia and Charles Sturt University have developed an algorithm to detect and intercept man-in-the-middle attacks on unmanned military robots. MitM attacks are a type of cyberattack where the data traffic between two parties, in this case, the robot and its legitimate controllers, is intercepted either to eavesdrop or to inject false data in the stream.

A US Navy service member pleaded guilty yesterday to receiving thousands of dollars in bribes from a Chinese spymaster in exchange for passing on American military secrets. Petty Officer Wenheng Zhao, 26, aka Thomas Zhao, of Monterey Park, California, now faces up to 20 years in prison for two federal felony offenses: conspiring with a People's Republic of China intelligence officer, and receiving a bribe.

In this Help Net Security interview, James Murphy, the Director of the TechVets Programme at the Forces Employment Charity, discusses the challenges that military veterans face when transitioning from military to civilian life. We often find that many businesses are in high demand of cybersecurity skills, but additionally lack the soft skills that many from a military background can offer.
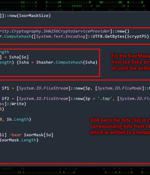
Ukrainian military entities are the target of a phishing campaign that leverages drone manuals as lures to deliver a Go-based open-source post-exploitation toolkit called Merlin. "Since drones or...

The risk of running obsolete code and hardware was highlighted after attackers exfiltrated data from a UK supplier of high-security fencing for military bases. The initial entry point? A Windows 7 PC. While the supplier, Wolverhampton-based Zaun, said it believed that no classified information was downloaded, reports indicated that attackers were able to obtain data that could be used to gain access to some of the UK's most sensitive military and research sites.

Cybersecurity and intelligence agencies from Australia, Canada, New Zealand, the U.K., and the U.S. on Thursday disclosed details of a mobile malware strain targeting Android devices used by the Ukrainian military. The malicious software, dubbed Infamous Chisel and attributed to a Russian state-sponsored actor called Sandworm, has capabilities to "Enable unauthorized access to compromised devices, scan files, monitor traffic, and periodically steal sensitive information."

Hackers working for the Main Directorate of the General Staff of the Armed Forces of the Russian Federation, more commonly known as the GRU, have been targeting Android devices in Ukraine with a new malicious framework named 'Infamous Chisel. The malware was first highlighted in a warning from the Ukrainian Security Service earlier this month about efforts from the Sandworm hacking group to penetrate military command systems.
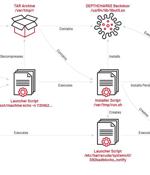
A suspected Chinese-nexus hacking group exploited a recently disclosed zero-day flaw in Barracuda Networks Email Security Gateway appliances to breach government, military, defense and aerospace, high-tech industry, and telecom sectors as part of a global espionage campaign. What's more, FOXTROT shares overlaps with an open-source rootkit called Reptile, which has been extensively used by multiple Chinese hacking crews in recent months.