Security News

Your profile can be used to present content that appears more relevant based on your possible interests, such as by adapting the order in which content is shown to you, so that it is even easier for you to find content that matches your interests. Content presented to you on this service can be based on your content personalisation profiles, which can reflect your activity on this or other services, possible interests and personal aspects.

Fascinating analysis of the use of drones on a modern battlefield-that is, Ukraine-and the inability of the US Air Force to react to this change. The Air Force is planning to buy 1,763 of the aircraft, which will remain in service through the year 2070.

Two US government agencies, the Cybersecurity and Infrastructure Security Agency and Federal Bureau of Investigation, warned on Wednesday that drones made in China could be used to gather information on critical infrastructure. How Wi-Fi spy drones snooped on financial firm FCC suggests licensing 5GHz spectrum to drone operators Wing, Alphabet's drone delivery unit, designs bigger bird to deliver pasta, faster US lawmakers have Chinese LiDAR on their threat-detection radar.

Facing an enemy with superior numbers of troops and armor, the Ukrainian defenders are holding on with the help of tiny drones flown by operators like Firsov that, for a few hundred dollars, can deliver an explosive charge capable of destroying a Russian tank worth more than $2 million. A typical FPV weighs up to one kilogram, has four small engines, a battery, a frame and a camera connected wirelessly to goggles worn by a pilot operating it remotely.

A PhD student has been found guilty of building a potentially deadly drone for Islamic State terrorists, in part using his home 3D printer. The prosecution said he had designed the single-use, video-transmitting "Kamikaze" drone "Somewhat inspired by the design of the Tomahawk missile," and used a 3D printer to build the wings.

DARPA's extended-duration unmanned undersea vehicle is having its first aquatic excursion to test if this naval drone has wings, er, fins. The splash test was part of DARPA's Manta Ray program for America's next-generation of undersea power projection, with PacMar Technologies and Northrop Grumman each building their own prototype UUVs.
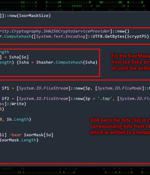
Ukrainian military entities are the target of a phishing campaign that leverages drone manuals as lures to deliver a Go-based open-source post-exploitation toolkit called Merlin. "Since drones or...

Unmanned aircraft systems, more commonly known as drones, have quite literally taken off by performing many new and inventive commercial applications. Delivering packages, recording terrain, reporting news, documenting wildlife and even providing internet access are just a few of the functions drones can offer.

China introduced restrictions on Monday that mean would-be exporters will require a license to ship certain drones and related equipment out of the Middle Kingdom. A spokesperson clarified that all civilian drones that are not included in the control are banned from export for military purposes, according to the Ministry of Commerce website.

Drones that don't have any known security weaknesses could be the target of electromagnetic fault injection attacks, potentially enabling a threat actor to achieve arbitrary code execution and compromise their functionality and safety. Side-channel attacks typically work by indirectly gathering information about a target system by exploiting unintended information leakages arising from variations in power consumption, electromagnetic emanations, and the time it takes to perform different mathematical operations.