Security News

Vulnerable Docker services are being targeted by a novel campaign in which the threat actors are deploying XMRig cryptocurrency miner as well as the 9Hits Viewer software as part of a...

The Russia-linked threat actor known as COLDRIVER has been observed evolving its tradecraft to go beyond credential harvesting to deliver its first-ever custom malware written in the Rust...

Russian cyberspies linked to the Kremlin's Federal Security Service are moving beyond their usual credential phishing antics and have developed a custom backdoor that they started delivering via email as far back as November 2022, according to Google's Threat Analysis Group. "TAG has observed SPICA being used as early as September 2023, but believe that COLDRIVER's use of the backdoor goes back to at least November 2022," the Chocolate Factory's threat hunting team said in an analysis published today.

Google says the ColdRiver Russian-backed hacking group is pushing previously unknown backdoor malware using payloads masquerading as a PDF decryption tool. "COLDRIVER presents these documents as a new op-ed or other type of article that the impersonation account is looking to publish, asking for feedback from the target. When the user opens the benign PDF, the text appears encrypted," Google TAG said.

Microsoft says that a subgroup of the notorious APT35 Iranian-backed state hackers are targeting high-profile employees of research organizations and universities across Europe and the United States in spearphishing attacks pushing new MediaPL backdoor malware. MediaPL is a highly sophisticated malware strain designed to compromise the security of researchers and their data. The attackers have specifically targeted individuals involved in cutting-edge research, seeking unauthorized access to sensitive information. Microsoft's dedicated security teams have dissected the malware to better understand its functionality and devise effective countermeasures.

A previously unknown cybercrime syndicate named 'Bigpanzi' has been making significant money by infecting Android TV and eCos set-top boxes worldwide since at least 2015. Bigpanzi infects the devices via firmware updates or backdoored apps the users are tricked into installing themselves, as highlighted in a September 2023 report by Dr. Web.

CISA and the FBI warned today that threat actors using Androxgh0st malware are building a botnet focused on cloud credential theft and using the stolen information to deliver additional malicious payloads. "Androxgh0st is a Python-scripted malware primarily used to target.env files that contain confidential information, such as credentials for various high profile applications," the two agencies cautioned.
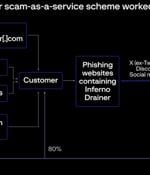
The operators behind the now-defunct Inferno Drainer created more than 16,000 unique malicious domains over a span of one year between 2022 and 2023. The scheme “leveraged high-quality phishing...

A Phemedrone information-stealing malware campaign exploits a Microsoft Defender SmartScreen vulnerability to bypass Windows security prompts when opening URL files. The Microsoft Defender flaw exploited in the Phemedrone campaign is CVE-2023-36025, which was fixed during the November 2023 Patch Tuesday, where it was marked as actively exploited in attacks.

Criminals are exploiting a Windows Defender SmartScreen bypass vulnerability to infect PCs with Phemedrone Stealer, a malware strain that scans machines for sensitive information - passwords, cookies, authentication tokens, you name it - to grab and leak. That file exploits CVE-2023-36025 to evade the Windows SmartScreen as it downloads and opens a.cpl file, which is a Windows control panel item.