Security News

A new Android banking malware named 'SoumniBot' is using a less common obfuscation approach by exploiting weaknesses in the Android manifest extraction and parsing procedure. The method enables SoumniBot to evade standard security measures found in Android phones and perform info-stealing operations.

The threat actor tracked as TA558 has been observed leveraging steganography as an obfuscation technique to deliver a wide range of malware such as Agent Tesla, FormBook, Remcos RAT, LokiBot,...

The U.S. Cybersecurity and Infrastructure Security Agency has released a new version of "Malware Next-Gen," now allowing the public to submit malware samples for analysis by CISA. Malware Next-Gen is a malware analysis platform that examines malware samples for suspicious artifacts. "The Cybersecurity and Infrastructure Security Agency announces today a new release of our malware analysis system, called Malware Next-Gen, which allows any organization to submit malware samples and other suspicious artifacts for analysis," reads the announcement.

A threat actor is using a PowerShell script that was likely created with the help of an artificial intelligence system such as OpenAI's ChatGPT, Google's Gemini, or Microsoft's CoPilot. Accessing the shortcut file triggered PowerShell to run a remote script.

Cybersecurity researchers have discovered a new Raspberry Robin campaign wave that propagates the malware through malicious Windows Script Files (WSFs) since March 2024. "Historically, Raspberry...
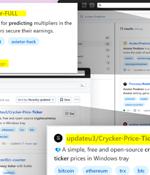
Threat actors are now taking advantage of GitHub's search functionality to trick unsuspecting users looking for popular repositories into downloading spurious counterparts that serve malware. The...

Threat actors are abusing GitHub automation features and malicious Visual Studio projects to push a new variant of the "Keyzetsu" clipboard-hijacking malware and steal cryptocurrency payments. Users downloading files from those repositories become infected with malware hidden within Visual Studio project files and stealthily executed during the project build.

Microsoft has fixed two actively exploited zero-day vulnerabilities during the April 2024 Patch Tuesday, although the company failed to initially tag them as such. "Just as we did in 2022, we immediately reported our findings to the Microsoft Security Response Center. After validating our discovery, the team at Microsoft has added the relevant files to its revocation list," Budd said.

Cybersecurity researchers have discovered an intricate multi-stage attack that leverages invoice-themed phishing decoys to deliver a wide range of malware such as Venom RAT, Remcos RAT, XWorm,...

Threat actors are actively scanning and exploiting a pair of security flaws that are said to affect as many as 92,000 internet-exposed D-Link network-attached storage (NAS) devices. Tracked...