Security News
Cybersecurity researchers have discovered that the malware known as BLOODALCHEMY used in attacks targeting government organizations in Southern and Southeastern Asia is in fact an updated version...

A new report from IBM X-Force exposes changes in the Grandoreiro malware landscape. The banking trojan is now capable of targeting more than 1,500 global banks in more than 60 countries, and it has been updated with new features.

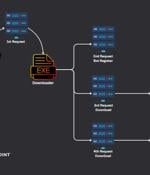
A new attack campaign dubbed CLOUD#REVERSER has been observed leveraging legitimate cloud storage services like Google Drive and Dropbox to stage malicious payloads. "The VBScript and PowerShell...
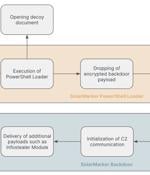
The persistent threat actors behind the SolarMarker information-stealing malware have established a multi-tiered infrastructure to complicate law enforcement takedown efforts, new findings from...
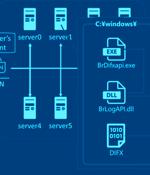
Multiple threat actors are weaponizing a design flaw in Foxit PDF Reader to deliver a variety of malware such as Agent Tesla, AsyncRAT, DCRat, NanoCore RAT, NjRAT, Pony, Remcos RAT, and XWorm....

A "multi-faceted campaign" has been observed abusing legitimate services like GitHub and FileZilla to deliver an array of stealer malware and banking trojans such as Atomic (aka AMOS), Vidar,...

Cybersecurity researchers have observed a spike in email phishing campaigns starting early March 2024 that delivers Latrodectus, a nascent malware loader believed to be the successor to the IcedID...

The banking trojan "Grandoreiro" is spreading in a large-scale phishing campaign in over 60 countries, targeting customer accounts of roughly 1,500 banks. In January 2024, an international law enforcement operation involving Brazil, Spain, Interpol, ESET, and Caixa Bank announced the disruption of the malware operation, which had been targeting Spanish-speaking countries since 2017 and caused $120 million in losses.

In January 2024, an international law enforcement operation involving Brazil, Spain, Interpol, ESET, and Caixa Bank announced the disruption of the malware operation, which had been targeting Spanish-speaking countries since 2017 and caused $120 million in losses. IBM X-Force noticed several new features and significant updates in the latest variant of the Grandoreiro banking trojan, making it a more evasive and effective threat.

Security researchers discovered two previously unseen backdoors dubbed LunarWeb and LunarMail that were used to compromise a European government's diplomatic institutions abroad. The pieces of malware have been used to breach the Ministry of Foreign Affairs of a European country with diplomatic missions in the Middle East and have been active since at least 2020. Researchers at cybersecurity company ESET believe that the backdoors may be connected to the Russian state-sponsored hacker group Turla, although attribution has medium confidence at this point.