Security News
A stealthy Unified Extensible Firmware Interface bootkit called BlackLotus has become the first publicly known malware capable of bypassing Secure Boot defenses, making it a potent threat in the cyber landscape. "This bootkit can run even on fully up-to-date Windows 11 systems with UEFI Secure Boot enabled," Slovak cybersecurity company ESET said in a report shared with The Hacker News.
The RIG exploit kit touched an all-time high successful exploitation rate of nearly 30% in 2022, new findings reveal. Exploit kits are programs used to distribute malware to large numbers of victims by taking advantage of known security flaws in commonly-used software such as web browsers.

A new ChromeLoader malware campaign has been observed being distributed via virtual hard disk files, marking a deviation from the ISO optical disc image format. "These VHD files are being distributed with filenames that make them appear like either hacks or cracks for Nintendo and Steam games," AhnLab Security Emergency response Center said in a report last week.

Government entities in Asia-Pacific and North America are being targeted by an unknown threat actor with an off-the-shelf malware downloader known as PureCrypter to deliver an array of information stealers and ransomware. "The PureCrypter campaign uses the domain of a compromised non-profit organization as a command-and-control to deliver a secondary payload," Menlo Security researcher Abhay Yadav said.

Analyzing wiper malware data reveals a trend of cyber adversaries consistently using destructive attack techniques against their targets. Later in the year, wiper malware expanded into other countries, fueling a 53% increase in wiper activity from Q3 to Q4 alone.

A threat actor has been targeting government entities with PureCrypter malware downloader that has been seen delivering multiple information stealers and ransomware strains. "The campaign was found to have delivered several types of malware including Redline Stealer, AgentTesla, Eternity, Blackmoon and Philadelphia Ransomware," the researchers say.

A Russian national accused of developing the NLBrute brute-force hacking tool has made his first court appearance this week in Florida over accusations that he used the tool to spawn a criminal empire. Dariy Pankov, also known as "Dpxaker," created the NLBrute malware that cracked the Windows credentials of improperly secured Remote Desktop Protocol systems through the brute-force technique of throwing massive numbers of password guesses at them, according to the US Department of Justice.

Security researchers discovered a cryptomining operation targeting macOS with a malicious version of Final Cut Pro that remains largely undetected by antivirus engines. From the first generation, the malware used an i2p network layer for command and control communications to anonymize traffic.

A Russian malware developer accused of creating and selling the NLBrute password-cracking tool was extradited to the United States after being arrested in the Republic of Georgia last year on October 4. "The powerful malware was capable of compromising protected computers by decrypting login credentials, such as passwords," the Justice Department said in a press release on Wednesday.
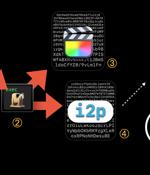
Trojanized versions of legitimate applications are being used to deploy evasive cryptocurrency mining malware on macOS systems. "This malware makes use of the Invisible Internet Project to download malicious components and send mined currency to the attacker's wallet," Jamf researchers Matt Benyo, Ferdous Saljooki, and Jaron Bradley said in a report shared with The Hacker News.