Security News
An Iranian state-sponsored actor has been observed scanning and attempting to abuse the Log4Shell flaw in publicly-exposed Java applications to deploy a hitherto undocumented PowerShell-based modular backdoor dubbed "CharmPower" for follow-on post-exploitation. Log4Shell aka CVE-2021-44228 concerns a critical security vulnerability in the popular Log4j logging library that, if successfully exploited, could lead to remote execution of arbitrary code on compromised systems.

The U.S. Cyber Command on Wednesday officially confirmed MuddyWater's ties to the Iranian intelligence apparatus, while simultaneously detailing the various tools and tactics adopted by the espionage actor to burrow into victim networks. "MuddyWater has been seen using a variety of techniques to maintain access to victim networks," USCYBERCOM's Cyber National Mission Force said in a statement.

US Cyber Command has officially linked the Iranian-backed MuddyWatter hacking group to Iran's Ministry of Intelligence and Security. MOIS is the Iran government's leading intelligence agency, tasked with coordinating the country's intelligence and counterintelligence, as well as covert actions supporting the Islamic regime's goals beyond Iran's borders.
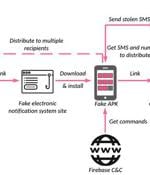
Socially engineered SMS messages are being used to install malware on Android devices as part of a widespread phishing campaign that impersonates the Iranian government and social security services to make away with credit card details and steal funds from victims' bank accounts. "The malicious application not only collects the victim's credit card numbers, but also gains access to their 2FA authentication SMS, and turn[s] the victim's device into a bot capable of spreading similar phishing SMS to other potential victims," Check Point researcher Shmuel Cohen said in a new report published Wednesday.

Attackers are impersonating the Iranian government in a widespread SMS phishing campaign that is defrauding thousands of Android users by installing malware on their devices that can steal their credit card data and siphon money from financial accounts. The campaign is first delivered as a standard smishing attack, using socially engineered SMS messages sent to a potential victim's device to lure them to a malicious website, researchers said.

The U.S. government on Thursday unsealed an indictment that accused two Iranian nationals of their involvement in cyber-enabled disinformation and threat campaign orchestrated to interfere in the 2020 presidential elections by gaining access to confidential voter information from at least one state election website. The two defendants in question - Seyyed Mohammad Hosein Musa Kazemi, 24, and Sajjad Kazemi, 27 - have been charged with conspiracy to commit computer fraud and abuse, intimidate voters, and transmit interstate threats, voter intimidation, transmission of interstate threats, with Kazemi additionally charged with unauthorized computer intrusion.

Cybersecurity agencies from Australia, the U.K., and the U.S. on Wednesday released a joint advisory warning of active exploitation of Fortinet and Microsoft Exchange ProxyShell vulnerabilities by Iranian state-sponsored actors to gain initial access to vulnerable systems for follow-on activities, including data exfiltration and ransomware. The threat actor is believed to have leveraged multiple Fortinet FortiOS vulnerabilities dating back to March 2021 as well as a remote code execution flaw affecting Microsoft Exchange Servers since at least October 2021, according to the U.S. Cybersecurity and Infrastructure Security Agency, the Federal Bureau of Investigation, the Australian Cyber Security Centre, and the U.K.'s National Cyber Security Centre.

The U.S. Department of Justice has unsealed charges against two Iranian nationals for cyberattacks against the U.S. 2020 presidential campaign, and there's a $10 million reward offered for information on their activities. Kazemi and Kashian allegedly breached at least one state election website and attempted to access 110 others, sent threatening emails to voters, distributed a disinformation video about election infrastructure vulnerabilities, and gained access to a U.S. media company's network, according to law enforcement.

The U.S. Department of State is offering a $10 million reward for information about the activities of two Iranian nationals charged for cyber activity intended to "Intimidate and influence" American voters during the 2020 U.S. presidential campaign. An indictment unsealed today by the Department of Justice alleges that between September and November 2020, 24-year old Seyyed Mohammad Hosein Musa Kazemi and 27-year old Sajjad Kashian obtained information of more than 100,000 U.S. voters and used it "Sow discord among Americans."

Microsoft says Iranian-backed hacking groups have increasingly attempted to compromise IT services companies this year to steal credentials they could use to breach the systems of downstream clients. According to security analysts at Microsoft Threat Intelligence Center and Digital Security Unit, this activity is part of a wider espionage objective to compromise entities of interest to the Iranian regime.