Security News

A phishing campaign that security researchers named SmugX and attributed to a Chinese threat actor has been targeting embassies and foreign affairs ministries in the UK, France, Sweden, Ukraine, Czech, Hungary, and Slovakia, since December 2022. The lures used in the SmugX campaign betray the threat actor's target profile and indicates espionage as the likely objective of the campaign.

A Chinese nation-state group has been observed targeting Foreign Affairs ministries and embassies in Europe using HTML smuggling techniques to deliver the PlugX remote access trojan on compromised systems. "The campaign uses new delivery methods to deploy a new variant of PlugX, an implant commonly associated with a wide variety of Chinese threat actors," Check Point said.
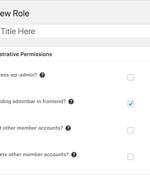
As many as 200,000 WordPress websites are at risk of ongoing attacks exploiting a critical unpatched security vulnerability in the Ultimate Member plugin. Ultimate Member is a popular plugin that facilitates the creation of user-profiles and communities on WordPress sites.

Hackers exploit a zero-day privilege escalation vulnerability in the 'Ultimate Member' WordPress plugin to compromise websites by bypassing security measures and registering rogue administrator accounts. Ultimate Member is a user profile and membership plugin that facilitates sign-ups and building communities on WordPress sites, and it currently has over 200,000 active installations.
Charming Kitten, the nation-state actor affiliated with Iran's Islamic Revolutionary Guard Corps, has been attributed to a bespoke spear-phishing campaign that delivers an updated version of a fully-featured PowerShell backdoor called POWERSTAR. "There have been improved operational security measures placed in the malware to make it more difficult to analyze and collect intelligence," Volexity researchers Ankur Saini and Charlie Gardner said in a report published this week. Recent intrusions orchestrated by Charming Kitten have made use of other implants such as PowerLess and BellaCiao, suggesting that the group is utilizing an array of espionage tools at its disposal to realize its strategic objectives.

The North Korea-aligned threat actor known as Andariel leveraged a previously undocumented malware called EarlyRat in attacks exploiting the Log4j Log4Shell vulnerability last year. "Andariel infects machines by executing a Log4j exploit, which, in turn, downloads further malware from the command-and-control server," Kaspersky said in a new report.

If you say THE Twitter hack, everyone knows you mean the one that happened in July 2020, when a small group of cybercriminals ended up in control of a small number of Twitter accounts and used them to talk up a cryptocoin fraud. SIM swaps are where a criminal sweet-talks, bribes or coerces a mobile phone provider into issuing them with a "Replacment" SIM card for someone else's number, typically under the guise of wanting to buy a new phone or urgently needing to replace a lost SIM. The victim's SIM card goes dead, and the crook starts receiving their calls and text messages, notably including any two-factor authentication codes needed for secure logins or password resets.

The New York City Department of Education says hackers stole documents containing the sensitive personal information of up to 45,000 students from its MOVEit Transfer server.The Clop ransomware gang has claimed responsibility for the CVE-2023-34362 MOVEit Transfer attacks on June 5 in a statement shared with BleepingComputer, with the cybercrime gang saying it breached the MOVEit servers of "Hundreds of companies."

Microsoft has disclosed that it's detected a spike in credential-stealing attacks conducted by the Russian state-affiliated hacker group known as Midnight Blizzard. The group, which drew worldwide attention for the SolarWinds supply chain compromise in December 2020, has continued to rely on unseen tooling in its targeted attacks aimed at foreign ministries and diplomatic entities.

The newly discovered Chinese nation-state actor known as Volt Typhoon has been observed to be active in the wild since at least mid-2020, with the hacking crew linked to never-before-seen tradecraft to retain remote access to targets of interest. "The adversary consistently employed ManageEngine Self-service Plus exploits to gain initial access, followed by custom web shells for persistent access, and living-off-the-land techniques for lateral movement," the cybersecurity company said.