Security News

An "Extremely sophisticated" Chinese-speaking advanced persistent threat actor dubbed LuoYu has been observed using a malicious Windows tool called WinDealer that's delivered by means of man-on-the-side attacks. "Such attacks are especially dangerous and devastating because they do not require any interaction with the target to lead to a successful infection."

Microsoft on Thursday said it took steps to disable malicious activity stemming from abuse of OneDrive by a previously undocumented threat actor it tracks under the chemical element-themed moniker Polonium. In addition to removing the offending accounts created by the Lebanon-based activity group, the tech giant's Threat Intelligence Center said it suspended over 20 malicious OneDrive applications created and that it notified affected organizations.

The Microsoft Digital Crimes Unit has disrupted a spear-phishing operation linked to an Iranian threat actor tracked as Bohrium that targeted customers in the U.S., Middle East, and India. Bohrium has targeted organizations from a wide range of industry sectors, including tech, transportation, government, and education, according to Amy Hogan-Burney, the General Manager of Microsoft DCU. Microsoft has taken down 41 domains used in this campaign to establish a command and control infrastructure that enabled the attackers to deploy malicious tools designed to help them gain access to targets' devices and exfiltrate stolen information from compromised systems.

Atlassian has warned of a critical unpatched remote code execution vulnerability impacting Confluence Server and Data Center products that it said is being actively exploited in the wild. "Atlassian has been made aware of current active exploitation of a critical severity unauthenticated remote code execution vulnerability in Confluence Data Center and Server," it said in an advisory.
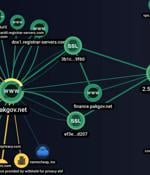
The threat actor known as SideWinder has added a new custom tool to its arsenal of malware that's being used in phishing attacks against Pakistani public and private sector entities. The custom tool identified by Group-IB, dubbed SideWinder.

Microsoft said it blocked a Lebanon-based hacking group it tracks as Polonium from using the OneDrive cloud storage platform for data exfiltration and command and control while targeting and compromising Israelian organizations. Throughout the attacks that mainly targeted Israel's critical manufacturing, IT, and defense industry sectors since February 2022, Polonium operators have also likely coordinated their hacking attempts with multiple Iran-linked threat actors, according to Redmond's analysis.

A Chinese-speaking hacking group known as LuoYu is infecting victims WinDealer information stealer malware deployed by switching legitimate app updates with malicious payloads in man-on-the-side attacks. LuoYu has switched to abusing the automatic update mechanism of their victims' apps after previously pushing malware in easier to pull-off watering-hole attacks where they would use compromised local news sites as infection vectors.
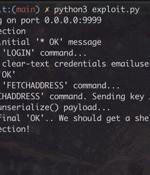
A new unpatched security vulnerability has been disclosed in the open-source Horde Webmail client that could be exploited to achieve remote code execution on the email server simply by sending a specially crafted email to a victim. "Once the email is viewed, the attacker can silently take over the complete mail server without any further user interaction," SonarSource said in a report shared with The Hacker News.

Another link discovered by Group-IB downloaded from Google Play, the official Android app store, a fake version of the 'Secure VPN' app, which is still present on Google Play at the time of writing and has just over 10 downloads. The researchers note that the description available for SideWinder's fake Secure VPN app has been copied from the legitimate NordVPN app.

An advanced persistent threat actor aligned with Chinese state interests has been observed weaponizing the new zero-day flaw in Microsoft Office to achieve code execution on affected systems. "TA413 CN APT spotted exploiting the Follina zero-day using URLs to deliver ZIP archives which contain Word Documents that use the technique," enterprise security firm Proofpoint said in a tweet.