Security News

Decentralized money lender zkLend suffered a breach where threat actors exploited a smart contract flaw to steal 3,600 Ethereum, worth $9.5 million at the time. [...]

North Korean state actor 'Kimsuky' (aka 'Emerald Sleet' or 'Velvet Chollima') has been observed using a new tactic inspired from the now widespread ClickFix campaigns. [...]

The North Korea-linked threat actor known as Kimsuky has been observed using a new tactic that involves deceiving targets into running PowerShell as an administrator and then instructing them to...

The Sandworm Russian military cyber-espionage group is targeting Windows users in Ukraine with trojanized Microsoft Key Management Service (KMS) activators and fake Windows updates. [...]

Security researchers at Bishop Fox have published complete exploitation details for the CVE-2024-53704 vulnerability that allows bypassing the authentication mechanism in certain versions of the...

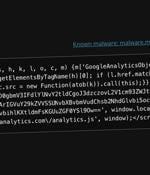
Threat actors have been observed leveraging Google Tag Manager (GTM) to deliver credit card skimmer malware targeting Magento-based e-commerce websites. Website security company Sucuri said the...

Threat actors have been observed exploiting multiple security flaws in various software products, including Progress Telerik UI for ASP.NET AJAX and Advantive VeraCore, to drop reverse shells and...

Software vendor Trimble is warning that hackers are exploiting a Cityworks deserialization vulnerability to remotely execute commands on IIS servers and deploy Cobalt Strike beacons for initial...

Threat actors have been observed exploiting recently disclosed security flaws in SimpleHelp's Remote Monitoring and Management (RMM) software as a precursor for what appears to be a ransomware...