Security News

Microsoft says the Sysrv botnet is now exploiting vulnerabilities in the Spring Framework and WordPress to ensnare and deploy cryptomining malware on vulnerable Windows and Linux servers. "The new variant, which we call Sysrv-K, sports additional exploits and can gain control of web servers" by exploiting various vulnerabilities, the Microsoft Security Intelligence team said in a Twitter thread. "These vulnerabilities, which have all been addressed by security updates, include old vulnerabilities in WordPress plugins, as well as newer vulnerabilities like CVE-2022-22947."

Security researchers have found a new post-exploitation framework that they dubbed IceApple, deployed mainly on Microsoft Exchange servers across a wide geography. The researchers observed IceApple being deployed after the threat actor obtains initial access to the network belonging to organizations in various activity sectors: technology, academic, and government.

Hackers have carried out over 65,000 attacks through Windows' Print Spooler exploit. A new report, from cybersecurity company Kaspersky, has found that cybercriminals conducted approximately 65,000 attacks through Windows' Print Spooler application between July 2021 and April 2022.

Threat actors have started exploiting a critical bug in the application service provider F5's BIG-IP modules after a working exploit of the vulnerability was publicly made available. A shodan query shared by security researcher Jacob Baines revealed thousands of exposed BIG-IP systems on the internet, which an attacker can leverage to exploit remotely.
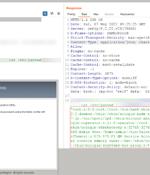
Days after F5 released patches for a critical remote code execution vulnerability affecting its BIG-IP family of products, security researchers are warning that they were able to create an exploit for the shortcoming. The critical security vulnerability impacts the following versions of BIG-IP products -.

Threat actors have started massively exploiting the critical vulnerability tracked as CVE-2022-1388, which affects multiple versions of all F5 BIG-IP modules, to drop malicious payloads. F5 last week released patches for the security issue, which affects the BIG-IP iControl REST authentication component.

Researchers have developed PoC exploits for CVE-2022-1388, a critical remote code execution bug affecting F5 BIG-IP multi-purpose networking devices/modules. We have reproduced the fresh CVE-2022-1388 in F5's BIG-IP. Successful exploitation could lead to RCE from an unauthenticated user.

Security researchers are warning F5 BIG-IP admins to immediately install the latest security updates after creating exploits for a recently disclosed critical CVE-2022-1388 remote code execution vulnerability. Last week, F5 disclosed a new critical remote code execution in BIG-IP networking devices tracked as CVE-2022-1388.

A new campaign leveraging an exploit kit has been observed abusing an Internet Explorer flaw patched by Microsoft last year to deliver the RedLine Stealer trojan. "When executed, RedLine Stealer performs recon against the target system and then exfiltrates data to a remote command and control server," Bitdefender said in a new report shared with The Hacker News.

Threat analysts have uncovered yet a new campaign that uses the RIG Exploit Kit to deliver the RedLine stealer malware. The threat actors use the exploit to compromise the machine and deploy RedLine, a cheap but powerful info-stealing malware widely circulated on Russian-speaking forums.